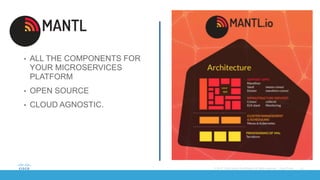
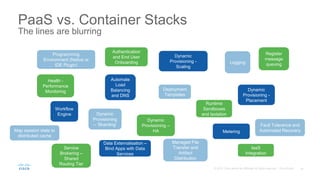
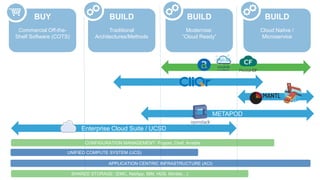
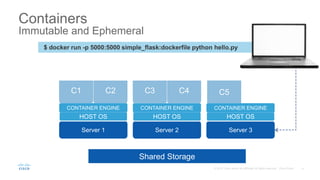
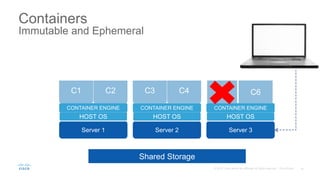
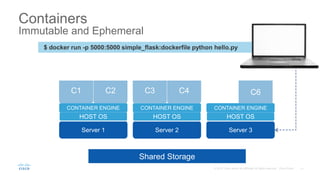
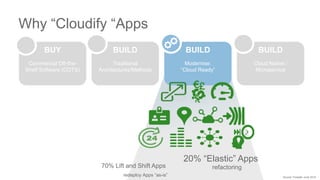
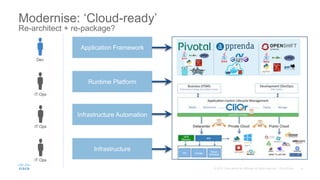
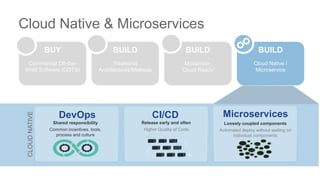
The document discusses building applications in modern cloud environments. It outlines four main approaches: buying commercial off-the-shelf software, building with traditional architectures/methods, modernizing existing applications to be "cloud ready", and building cloud native/microservice applications. It then discusses the benefits of containers over virtual machines for building distributed applications at scale in the cloud. Finally, it presents Mantl as an open source platform that provides all the components needed for a microservices architecture on top of infrastructure-as-a-service.


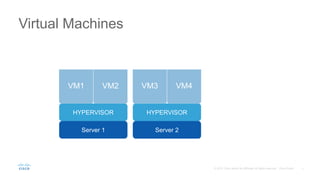
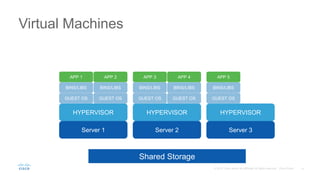
![Virtual Machines vs. Containers
Server 1
HYPERVISOR
GUEST OS
BINS/LIBS
APP 1
GUEST OS
BINS/LIBS
APP 2
VM1 VM2
Server 2
HOST OS
BINS/LIBS
APP 1
BINS/LIBS
APP 2
CONTAINER ENGINE
C1 C2
Runs Application on Virtual OS
Decouple Application from Infra
Environmental Consistency
Density
Boots in msec/sec
Runs OS on Virtual Hardware
Full OS in each VM
Boots in sec/mins
Dockerfile
FROM unbuntu:14.04
RUN apt-get install –y-redis-server
EXPOSE 6379
ENTRYPOINT [“usr/bin/redis-server”]](https://image.slidesharecdn.com/techhuddlepaassession-170406144157/85/Tech-huddle-paas_session-6-320.jpg)


![Containers at Scale
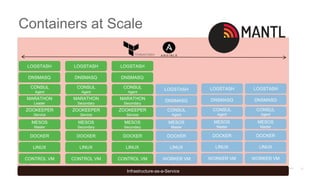
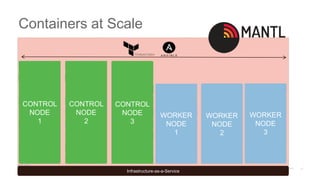
Infrastructure-as-a-Service
ZOOKEEPER
Service
CONSUL
Agent
MESOS
Secondary
ZOOKEEPER
Service
CONSUL
Agent
MESOS
Secondary
ZOOKEEPER
Service
MARATHON
Leader
MARATHON
Secondary
MARATHON
Secondary
CONSUL
Agent
CONSUL
Agent
CONSUL
Agent
CONTROL VM
LINUX
DOCKER
CONTROL VM
LINUX
DOCKER
CONTROL VM
LINUX
DOCKER
WORKER VM
LINUX
DOCKER
WORKER VM
LINUX
DOCKER
WORKER VM
LINUX
DOCKER
MESOS
Master
MESOS
Master
MESOS
Master
MESOS
Master
CONSUL
Agent
DNSMASQ
LOGSTASH
DNSMASQ
LOGSTASH
DNSMASQ
LOGSTASH
DNSMASQ
LOGSTASH
DNSMASQ
LOGSTASH
DNSMASQ
LOGSTASH
CONTROL
NODE
1
CONTROL
NODE
2
CONTROL
NODE
3
WORKER
NODE
3
WORKER
NODE
1
WORKER
NODE
2
What about:
• Initial host deployment and registry?
• External-to-[new] services comms and records?
• Service-to-Service comms?
• Log collection, forwarding, and analysis?
• Storage for ‘statefulness’?
• Virtual networking?
• Task scheduling?
• API management?](https://image.slidesharecdn.com/techhuddlepaassession-170406144157/85/Tech-huddle-paas_session-22-320.jpg)