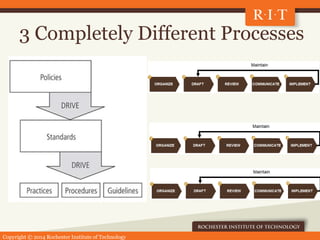
The document outlines a discussion on information security at the Rochester Institute of Technology, including the roles of the Information Security Office and the importance of establishing comprehensive security policies and awareness training. It emphasizes the need for various types of policies, standards, and practices to effectively manage information security risks while ensuring compliance with laws and regulations. Additionally, it covers penetration testing as a method to verify vulnerabilities within systems and the planning and reporting processes involved.