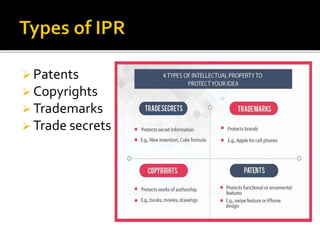
This document discusses various topics related to digital citizenship and responsible online behavior. It defines netiquette as etiquette for online behavior to avoid harming others. It discusses challenges of e-commerce like privacy, fraud and secure data transmission. It explains privacy and security measures like HTTPS, SSL used by merchants. It defines online fraud and security measures like not sharing login details. It discusses secure data transmission through encryption. It also discusses intellectual property, copyright, trademarks, patents, trade secrets and plagiarism. It defines digital property rights and different types of software licenses.