Top 6 Industries At Risk For Cyber Attacks
•
0 likes•2 views
There has been a remarkable shift in cloud adoption as businesses worldwide move their operations to the cloud. However, you don’t need to believe us—29% of organisations anticipate moving 75% of their workloads to the cloud in the coming months. Read More: https://instasafe.com/blog/top-10-cloud-security-issues-you-should-know/
Report
Share
Report
Share
Download to read offline
Recommended
The customer in question is one of the largest Business Process Outsourcing and IT Management firms in the
world. With a client base covering more than 400 multinational firms worldwide, the firm has more than 40000
employees working across multiple geographies. They deliver a wide array of Business Process Management
solutions across the verticals of accounting, human resources, customer interaction, and multiple such areas. Read More: https://instasafe.com/docs/ITES%20Case%20Study%202021.pdf
Delivering Remote Access for IT/ ITES Sector with InstaSafe Zero Trust Solutions

Delivering Remote Access for IT/ ITES Sector with InstaSafe Zero Trust SolutionsInstaSafe Technologies
Recommended
The customer in question is one of the largest Business Process Outsourcing and IT Management firms in the
world. With a client base covering more than 400 multinational firms worldwide, the firm has more than 40000
employees working across multiple geographies. They deliver a wide array of Business Process Management
solutions across the verticals of accounting, human resources, customer interaction, and multiple such areas. Read More: https://instasafe.com/docs/ITES%20Case%20Study%202021.pdf
Delivering Remote Access for IT/ ITES Sector with InstaSafe Zero Trust Solutions

Delivering Remote Access for IT/ ITES Sector with InstaSafe Zero Trust SolutionsInstaSafe Technologies
The customer in question is one of the largest Business Process Outsourcing and IT Management firms in the
world. With a client base covering more than 400 multinational firms worldwide, the firm has more than 40000
employees working across multiple geographies. They deliver a wide array of Business Process Management
solutions across the verticals of accounting, human resources, customer interaction, and multiple such areas. Read More: https://f2.leadsquaredcdn.com/t/insta/content/common/documents/Website/ITES%20Case%20Study%202021.pdfInstaSafe secures VoIP and applications access for the world's largest BPM firm

InstaSafe secures VoIP and applications access for the world's largest BPM firmInstaSafe Technologies
More Related Content
More from InstaSafe Technologies
The customer in question is one of the largest Business Process Outsourcing and IT Management firms in the
world. With a client base covering more than 400 multinational firms worldwide, the firm has more than 40000
employees working across multiple geographies. They deliver a wide array of Business Process Management
solutions across the verticals of accounting, human resources, customer interaction, and multiple such areas. Read More: https://f2.leadsquaredcdn.com/t/insta/content/common/documents/Website/ITES%20Case%20Study%202021.pdfInstaSafe secures VoIP and applications access for the world's largest BPM firm

InstaSafe secures VoIP and applications access for the world's largest BPM firmInstaSafe Technologies
More from InstaSafe Technologies (20)
InstaSafe vs Zscaler Private Access V2_Editable Verison

InstaSafe vs Zscaler Private Access V2_Editable Verison
Frequently Asked Questions on InstaSafe Zero Trust Solutions

Frequently Asked Questions on InstaSafe Zero Trust Solutions
Total visibility with InstaSafe : The Master Key to Zero Trust

Total visibility with InstaSafe : The Master Key to Zero Trust
InstaSafe Zero Trust - A better alternative to VPNs

InstaSafe Zero Trust - A better alternative to VPNs
InstaSafe Zero Trust solution - Multiple Scenarios and use cases

InstaSafe Zero Trust solution - Multiple Scenarios and use cases
InstaSafe Zero Trust Access - Key Features and Benefits

InstaSafe Zero Trust Access - Key Features and Benefits
InstaSafe secures VoIP and applications access for the world's largest BPM firm

InstaSafe secures VoIP and applications access for the world's largest BPM firm
Copy of 7 Security Tips to Manage Global Remote Workforces

Copy of 7 Security Tips to Manage Global Remote Workforces
Why Zero Trust is a Better Alternative to Business VPNs

Why Zero Trust is a Better Alternative to Business VPNs
Top 6 Ways To Secure Remote Access For Your Company

Top 6 Ways To Secure Remote Access For Your Company
Top 6 Industries At Risk For Cyber Attacks
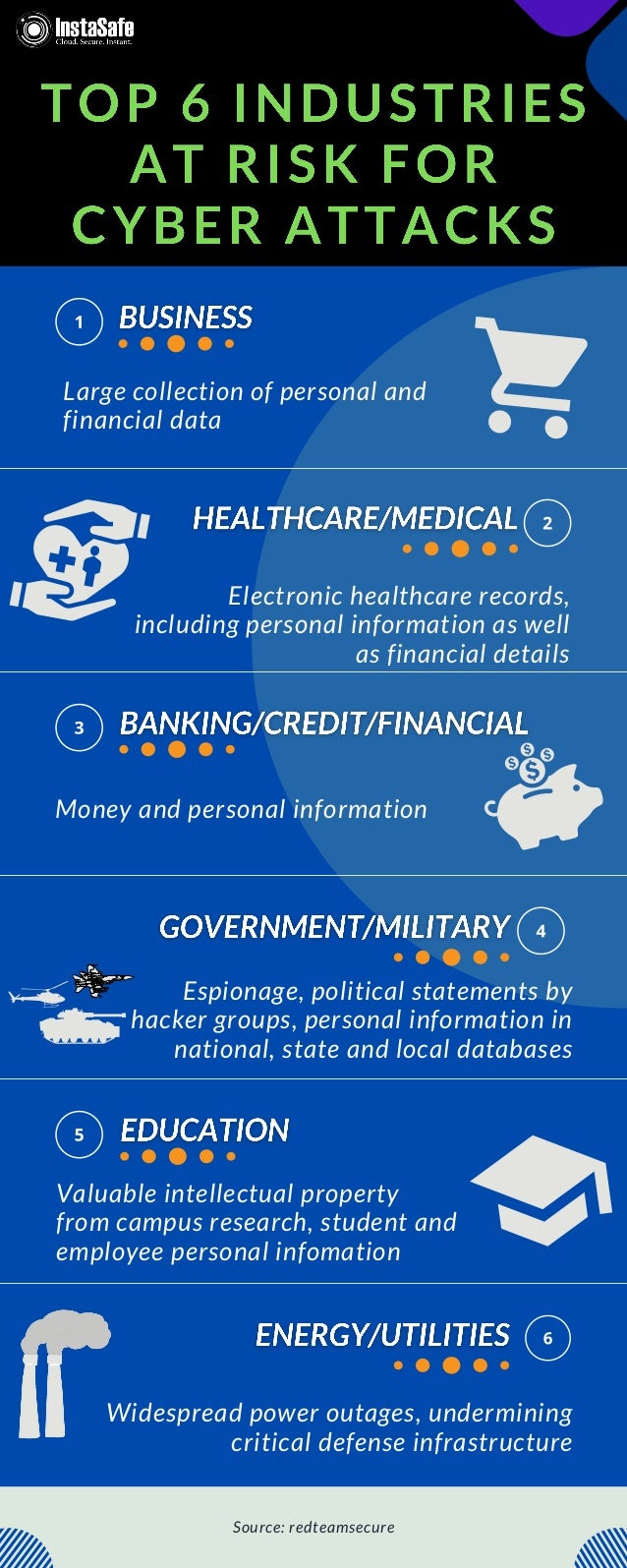
- 1. Espionage, political statements by hacker groups, personal information in national, state and local databases Money and personal information Large collection of personal and financial data Electronic healthcare records, including personal information as well as financial details Valuable intellectual property from campus research, student and employee personal infomation Source: redteamsecure Widespread power outages, undermining critical defense infrastructure