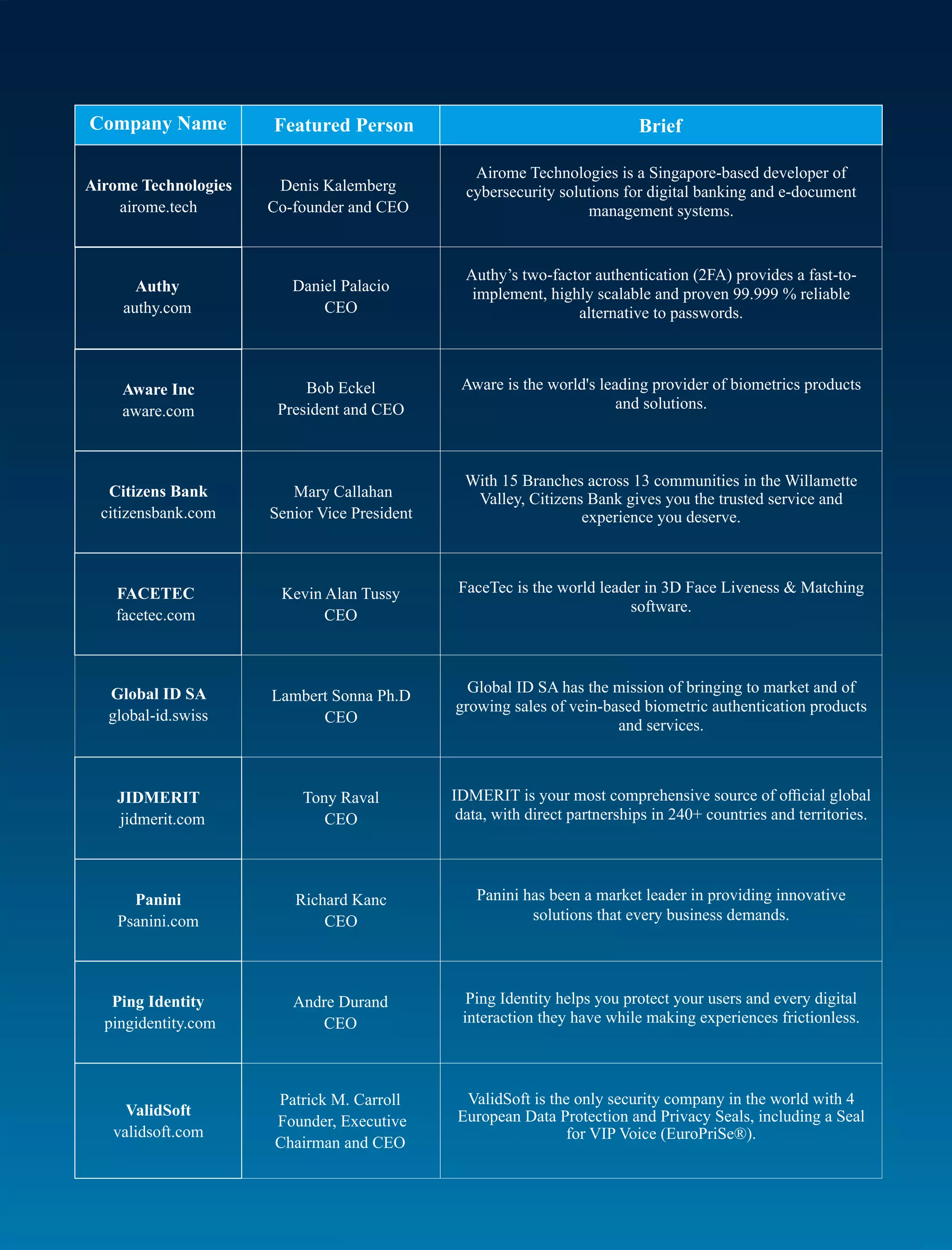
The document discusses the critical role of authentication solution providers in enhancing cybersecurity by offering robust and innovative measures to protect sensitive digital assets and ensure compliance with regulations. It highlights Aware, Inc. as a leading company in this space, emphasizing its expertise in biometric solutions that improve security and user experience while addressing the evolving challenges in data protection. The article also outlines the importance of choosing trusted providers and showcases the most reliable authentication solution companies of 2023.