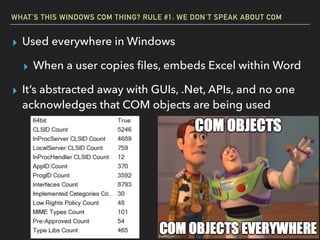
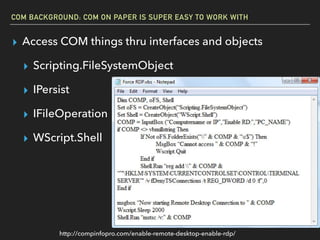
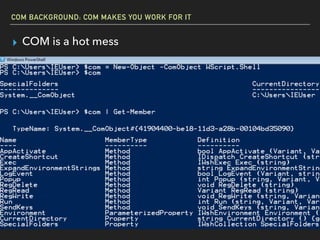
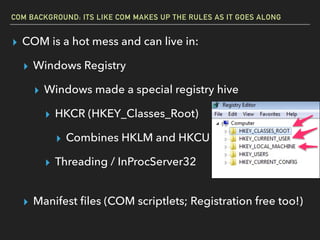
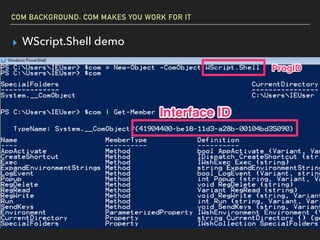
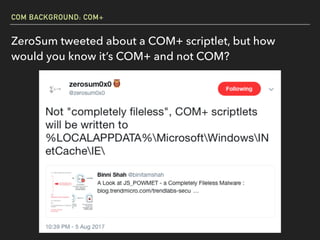
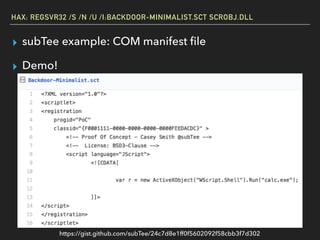
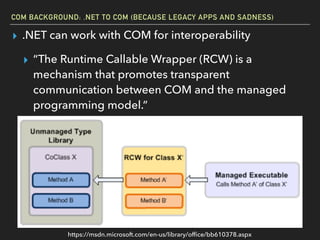
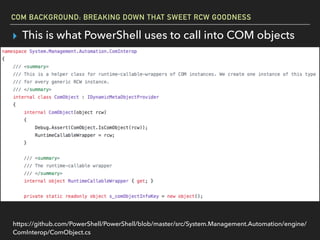
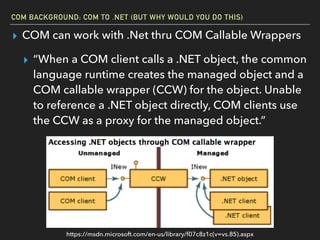
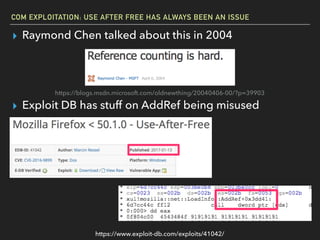
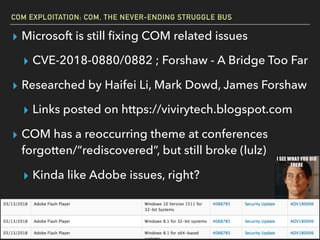
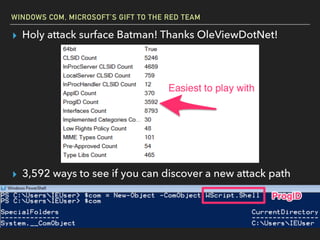
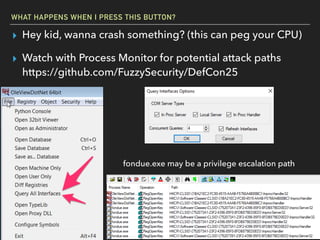
The document discusses Windows Component Object Model (COM) in detail, explaining its history, functionality, and exploitation potential. It covers various aspects of COM including its interoperability with .NET, exploitation techniques, and tools for researching weaknesses. The talk emphasizes the significance of COM in Windows systems and the need for both red and blue teams to understand its implications for security.