Iso 27001 2013 Standard Requirements
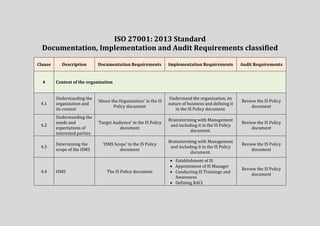
- 1. ISO 27001: 2013 Standard Documentation, Implementation and Audit Requirements classified Clause Description Documentation Requirements Implementation Requirements Audit Requirements 4 Context of the organization 4.1 Understanding the organization and its context ‘About the Organization’ in the IS Policy document Understand the organization, its nature of business and defining it in the IS Policy document. Review the IS Policy document 4.2 Understanding the needs and expectations of interested parties ‘Target Audience’ in the IS Policy document Brainstorming with Management and including it in the IS Policy document. Review the IS Policy document 4.3 Determining the scope of the ISMS ‘ISMS Scope’ in the IS Policy document Brainstorming with Management and including it in the IS Policy document. Review the IS Policy document 4.4 ISMS The IS Policy document Establishment of IS Appointment of IS Manager Conducting IS Trainings and Awareness Defining RACI Review the IS Policy document
- 2. Clause Description Documentation Requirements Implementation Requirements Audit Requirements 5 Leadership 5.1 Leadership and commitment ISMS budget allocations, Assignment of competent IS Manager and required staff Approval of the IS Policy Allocation of funds Appointment of IS Manager and other IS roles Review and approval of ISMS changes Review of ISMS performance Check for ISMS head in budget Identify IS Manager Board approval for ISMS implementation activities 5.2 Policy IS Policy Development of the IS Policy Review the IS Policy document 5.3 Organizational roles, responsibilities and authorities Appointment of IS Manager and required staff Defining ISMS reporting structure Defining RACI IS responsibilities in Employee JD Appointment of IS Manager and required competent staff Development of ISMS reporting line Development of RACI Defining employee common IS responsibilities Identify IS Manager Review ISMS reporting structure Review ISMS RACI Review Employment documents
- 3. Clause Description Documentation Requirements Implementation Requirements Audit Requirements 6 Planning 6.1 Actions to address risks and opportunities - - - 6.1.1 General ISMS Risk Management Methodology Defining and documenting ISMS Risk Management Methodology Review ISMS Risk Management Methodology 6.1.2 IS Risk Assessment Define Risk Assessment Process List of Risk Owners Develop and document Risk Assessment Process including defining risk acceptance criteria, identifying risk owners Review Risk Assessment Process 6.1.3 IS Risk Treatment Define Risk Treatment Process and SoA Develop and document Risk Treatment Process including development of SoA Review Risk Treatment Process 6.2 IS Objectives and planning to achieve them Objectives in the IS Policy document Defining IS objectives of relevant functions and levels of the organization Review IS Policy
- 4. Clause Description Documentation Requirements Implementation Requirements Audit Requirements 7 Support 7.1 Resources Appointment of required ISMS staff Allocation of budget Conducting Management Reviews Appointment of IS Manager, IS training and awareness Identify ISMS Staff Review ISMS staff responsibilities 7.2 Competence IS Manager Job Description IS Staff qualifications and experience Appointment of competent IS Manager and required staff Review IS Manager and staff qualifications 7.3 Awareness IS Training and Awareness activities (training materials, schedules, assessments, appreciations) Conducting staff IS Training and awareness activities Review staff IS Training and Awareness activities 7.4 Communication List of ISMS Interested Parties, and Communication Plan Identify and list ISMS Interested parties Gather communication requirements and develop a plan Review list of interested parties and ISMS Communications Plan 7.5 Documented Information - - -
- 5. Clause Description Documentation Requirements Implementation Requirements Audit Requirements 7.5.1 General All documents identified as necessary by the ISO and Organization 7.5.2 Creating and Updating ISMS Documentation Process Revision/Document History to be included in all ISMS documentation Document distribution List Define ISMS Documentation process Review ISMS Documentation process Check for Revision/Docume nt History in ISMS documentation 7.5.3 Control of documented information List of all ISMS related Documents (policies, processes, procedures) and Records (Decisions, Change Records, Communications, Reports, Alerts, Logs) Data Labeling process (distribution and access) Data Retention & Archival process Adding Revision/Document History for all ISMS documents (Labeling, Version control, list of changes) Identification and gathering of all ISMS related documents and records Defining controls for developing and maintaining documented information – including Revision/Document History, labeling, distribution, access, versioning and changes Review of ISMS Documents and Records Review documents labeling, distribution, version and change details
- 6. Clause Description Documentation Requirements Implementation Requirements Audit Requirements 8 Operation 8.1 Operational planning and control Documents related to the IS operational plans, processes, procedures, actions implemented ISMS Change Register IS Communications, logs and reports Third party security reports Identification of ISMS Operational plans and control activities Review ISMS operations and control activities 8.2 IS Risk Assessment Risk Assessment Reports Conducting Risk Assessment Review of periodic IS Risk Assessment reports 8.3 IS Risk Treatment Risk Treatment plans, actions and results Implementing Risk Treatment activities Review of IS Risk Treatment plans, actions and results 9 Performance Evaluation
- 7. Clause Description Documentation Requirements Implementation Requirements Audit Requirements 9.1 Monitoring, measurement, analysis and evaluation Documents, logs, periodic reports on IS Risks, Incidents and Changes Identifying various IS Metrics to be monitored and measured. Assigning monitoring responsibilities to the competent staff Review reports on various ISMS metrics, and measurements 9.2 Internal Audit Periodic Internal Audit Reports Defining Internal Audit Plans and procedures (including defining Audit Criteria (ISO 27001), conducting Internal Audits periodically and reporting to Management) Review Internal Audit reports and results 9.3 Management Review MR Meeting minutes/decision related to ISMS. Ensuring Management reviews ISMS performance periodically Management conducting periodic reviews on ISMS performance, status of previous issues, risk assessments reports, Audits, NCs, Corrective actions, and feedback) Review ISMS performance reviews Review results of MRs (Corrective actions) 10 Improvement
- 8. Clause Description Documentation Requirements Implementation Requirements Audit Requirements 10.1 Nonconformity and corrective action ISO 27001 ISMS NC Register along with corrective action details. Developing and maintaining an NC Register Defining procedures for ISMS NC corrective actions Review ISO ISMS NC Register and status of corrective actions and its results. 10.2 Continual improvement Periodic Risk Assessments reports, Audit reports, MRs and feedbacks. Defining processes for deriving ISMS improvements through periodic risk assessments, internal and external audits, periodic MRs and interested parties feedback Adding improvements to the ISMS policies, processes and procedures Review ISMS continual improvement on the basis of risk assessments, pervious audits reports, MRs and feedback.
- 9. The ISO 27001:2013 standard does not require the organizations to prepare a separate ISMS policy explicitly. However, the organizations can prepare it if they want. The organizations already having both IS Policy and ISMS Policy can continue or merge into one single IS Policy document with minor changes. About IS vs ISMS Information security (IS) is achieved through the implementation of an applicable set of controls. The controls are selected through the chosen risk management process and managed using an ISMS (Information Security Management System). The ISMS includes policies, processes, procedures, organizational structures, software and hardware to protect the identified information assets. - According to ISO 27000:2012 ISMS Vocabulary Document About IS Policy Vs ISMS Policy IS Policy is the responsibility of the Board / Senior Management. ISMS Policy is the responsibility of Executive Management. The board delegate IS responsibilities to the Management, which are achieved effective through establishing, operating, monitoring, reviewing, maintaining and improving the ISMS. - Explained in the PECB ISO 27001 Lead Implementer Course Material
