Cisco Annual Security Report Infographic
•
0 likes•602 views
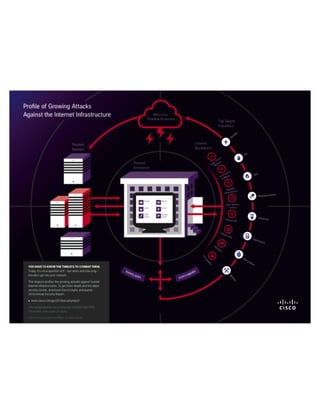
Growing Attacks Against the Internet Infrastructure. Learn more from the Cisco Annual Security Report: http://cs.co/CASR14_L
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
More Related Content
More from Cisco Security
More from Cisco Security (20)
Infonetics Network and Content Security Vendor Scorecard

Infonetics Network and Content Security Vendor Scorecard
Gartner Newsletter: Cisco TrustSec Deployed Across Enterprise Campus, Branch ...

Gartner Newsletter: Cisco TrustSec Deployed Across Enterprise Campus, Branch ...
The Evolution of and Need for Secure Network Access

The Evolution of and Need for Secure Network Access
City of Tomorrow Builds in Next-Generation Security

City of Tomorrow Builds in Next-Generation Security
Laser Pioneer Secures Network End-to-End to Protect Assets

Laser Pioneer Secures Network End-to-End to Protect Assets
Leveraging Context-Aware Security to Safeguard Patient Data

Leveraging Context-Aware Security to Safeguard Patient Data
Recently uploaded
Recently uploaded (20)
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
Understanding Discord NSFW Servers A Guide for Responsible Users.pdf

Understanding Discord NSFW Servers A Guide for Responsible Users.pdf
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
The Codex of Business Writing Software for Real-World Solutions 2.pptx

The Codex of Business Writing Software for Real-World Solutions 2.pptx
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
Factors to Consider When Choosing Accounts Payable Services Providers.pptx

Factors to Consider When Choosing Accounts Payable Services Providers.pptx
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
Powerful Google developer tools for immediate impact! (2023-24 C)

Powerful Google developer tools for immediate impact! (2023-24 C)
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
