Changing L andscape Of Cyber Attacks
•
0 likes•128 views
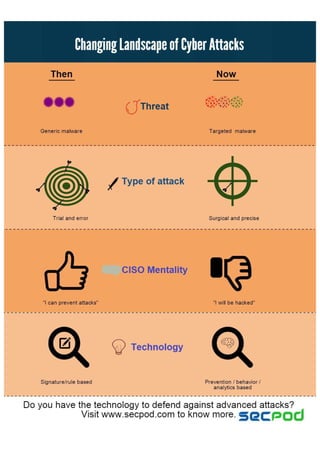
Infographic on how landscape of cyber attacks have changed to become more effective and precise.
Report
Share
Report
Share
Download to read offline
Recommended
My storyboard and trailer

I made my storyboard as a plan for when filming my trailer. This presentation shows how closely I followed it.
Making An Impact With PowerPoint

This is the slide deck (with added captions) from my From Cartoons to PowerPoint workshop - the ultimate guide to preparing and using powerful and effective visual aids.
Schedual 2

This production schedule outlines Laura Mckiernan's photography shoots for various dates in March, April and May. It lists the type of photos that will be taken, such as macro, landscape and portrait, the location of each shoot, and that a Canon 1100D will be used for all shoots.
Current Transcript Scan

This document summarizes the academic record of Jian Wu, including their grades and credits for courses completed in a Bachelor of Biotechnology degree at the University of Technology, Sydney. It shows that Jian has completed 132 credit points towards their degree with an overall GPA of 2.74. Courses are listed for each semester from 2013-2015, with subject names, results (grades of High Distinction, Distinction, Credit, etc.), marks, and credit points gained. Definitions of grading terms and scales are also provided at the top.
How BlueHat Cyber Uses SanerNow to Automate Patch Management and Beyond

It’s widely known that patch management is a major pain point for most businesses. IT teams struggle to keep systems patched and secure. Cyber-attacks are continuous and anti-virus protection alone isn’t effective.
Cyber hygiene best practices need to be followed to keep organizations secure and to prevent security breaches.
In this webinar, Chandrashekhar - SecPod’s Founder & CEO, Douglas Smith - BlueHat Cyber’s Senior Sales Director, and Greg Pottebaum - SecPod’s VP OEM & Strategic Alliances, demonstrate:
- How to efficiently reduce the cyber-attack surface of your business
- Simple strategies to improve your security management
- How Blue Hat Cyber uses SanerNow to automate patch management and secure their customer’s endpoints
Request a FREE Demo of SanerNow platform at:
www.secpod.com
About SecPod
SecPod is an endpoint security and management technology company. SecPod (Security Podium, incarnated as SecPod)
was founded in the year 2008. SecPod’s SanerNow platform and tools are used by MSPs and enterprises worldwide.
SecPod also licenses security technology to top security vendors through its SCAP Content Professional Feed.
Facebook: https://www.facebook.com/secpod/
LinkedIn: https://www.linkedin.com/company/secp...
Twitter: https://twitter.com/SecPod
Email us at info@secpod.com to get more details on how to secure your organisation from cyber attacks.
8 Types of Cyber Attacks That Can Bother CISOs in 2020

What are cyber attacks?
In simple terms, cyber attacks are attempts of disabling or stealing information from other computers, by gaining access to admin privileges to them.
Why should businesses be worried?
An average ransomware attack costs a company $5 million. Attackers target all types of businesses, small and large, healthcare, banking & finance, manufacturing, education, even government. The internet has made life a lot easier for business owners, at the same time it has made them easier to get hacked.
Security threats

Human threats pose the greatest risk to organizations, costing over $100 billion annually worldwide through hacking and social engineering. Network security threats like malware, viruses, and phishing attacks are common, with over 45% requiring user interaction via email. Physical security is often overlooked despite threats from theft, sabotage, and terrorism. Software threats can attack through logic bombs, trojans, worms and viruses.
Recommended
My storyboard and trailer

I made my storyboard as a plan for when filming my trailer. This presentation shows how closely I followed it.
Making An Impact With PowerPoint

This is the slide deck (with added captions) from my From Cartoons to PowerPoint workshop - the ultimate guide to preparing and using powerful and effective visual aids.
Schedual 2

This production schedule outlines Laura Mckiernan's photography shoots for various dates in March, April and May. It lists the type of photos that will be taken, such as macro, landscape and portrait, the location of each shoot, and that a Canon 1100D will be used for all shoots.
Current Transcript Scan

This document summarizes the academic record of Jian Wu, including their grades and credits for courses completed in a Bachelor of Biotechnology degree at the University of Technology, Sydney. It shows that Jian has completed 132 credit points towards their degree with an overall GPA of 2.74. Courses are listed for each semester from 2013-2015, with subject names, results (grades of High Distinction, Distinction, Credit, etc.), marks, and credit points gained. Definitions of grading terms and scales are also provided at the top.
How BlueHat Cyber Uses SanerNow to Automate Patch Management and Beyond

It’s widely known that patch management is a major pain point for most businesses. IT teams struggle to keep systems patched and secure. Cyber-attacks are continuous and anti-virus protection alone isn’t effective.
Cyber hygiene best practices need to be followed to keep organizations secure and to prevent security breaches.
In this webinar, Chandrashekhar - SecPod’s Founder & CEO, Douglas Smith - BlueHat Cyber’s Senior Sales Director, and Greg Pottebaum - SecPod’s VP OEM & Strategic Alliances, demonstrate:
- How to efficiently reduce the cyber-attack surface of your business
- Simple strategies to improve your security management
- How Blue Hat Cyber uses SanerNow to automate patch management and secure their customer’s endpoints
Request a FREE Demo of SanerNow platform at:
www.secpod.com
About SecPod
SecPod is an endpoint security and management technology company. SecPod (Security Podium, incarnated as SecPod)
was founded in the year 2008. SecPod’s SanerNow platform and tools are used by MSPs and enterprises worldwide.
SecPod also licenses security technology to top security vendors through its SCAP Content Professional Feed.
Facebook: https://www.facebook.com/secpod/
LinkedIn: https://www.linkedin.com/company/secp...
Twitter: https://twitter.com/SecPod
Email us at info@secpod.com to get more details on how to secure your organisation from cyber attacks.
8 Types of Cyber Attacks That Can Bother CISOs in 2020

What are cyber attacks?
In simple terms, cyber attacks are attempts of disabling or stealing information from other computers, by gaining access to admin privileges to them.
Why should businesses be worried?
An average ransomware attack costs a company $5 million. Attackers target all types of businesses, small and large, healthcare, banking & finance, manufacturing, education, even government. The internet has made life a lot easier for business owners, at the same time it has made them easier to get hacked.
Security threats

Human threats pose the greatest risk to organizations, costing over $100 billion annually worldwide through hacking and social engineering. Network security threats like malware, viruses, and phishing attacks are common, with over 45% requiring user interaction via email. Physical security is often overlooked despite threats from theft, sabotage, and terrorism. Software threats can attack through logic bombs, trojans, worms and viruses.
Hacking Internet of Things (IoT)

The document discusses vulnerabilities in IoT devices and provides examples of potential threats, including hacking a Jeep remotely and changing the target of a smart sniper rifle. It then summarizes challenges in securing IoT devices like limited resources, difficulty upgrading firmware, and lack of security software. Guidelines are provided for vendors, developers, and users to improve IoT security, such as using encryption, patching vulnerabilities, and educating users. Finally, the document demonstrates hacking a DTH set-top box by disturbing service, recording shows without permission, and stealing recordings.
WHY MSSPs LOVE OUR SOLUTION

Managed security service providers (MSSPs) value the Saner Business endpoint security solution for its ability to:
1) Find and eliminate vulnerabilities across networks in an automated and simple way.
2) Offer discrete security services and support regulatory compliance standards through continual assessment and remediation.
3) Provide continuous monitoring and detection of advanced threats that other solutions may overlook.
Many products-no-security (1)

The document discusses the challenges of managing IT security with many individual point products that have overlapping functionality and features. It introduces the SecPod SanerNow platform as a single platform approach for provisioning various security and endpoint management tools on demand to address specific tasks in a simpler and more cost-effective manner. Key benefits highlighted include reducing costs by up to 60%, easing management and improving security through continuous monitoring, vulnerability assessment, and threat detection and response capabilities.
SanerNow Endpoint Management

SanerNow Endpoint Management (EM) is a cloud-delivered
service that allows complete control over all your endpoint
systems. It provides visibility into the status of endpoints and
equips you with hundreds of built-in checks. SanerNow
Endpoint Management provides necessary features for
managing endpoints.
SanerNow Asset Management

SanerNow Asset Management (AM) is a cloud-delivered
service that tracks assets installed on hosts, the open
vulnerabilities in the OS and applications, their patch or update
levels, and prioritizes remediation tasks - all critical to the
deep visibility required to prevent attacks and data breaches.
SanerNow Patch Management

SanerNow Patch Management (PM) is a cloud-delivered
service that identifies and automatically rolls out patches
according to rules and jobs defined by the user. If necessary, it
automatically reboots systems after applying patches and can
roll back installed patches. SanerNow’s patch management
process is timely, responsive and systematically managed.
SanerNow Vulnerability Management

SanerNow Vulnerability Management (VM) is a cloud delivered
service that performs an automated daily vulnerability scan. Organizations can discover their threat and vulnerability risk in less than five minutes. SanerNow VM provides continuous visibility into IT systems. Its time-testedSCAP Feed database delivers comprehensive vulnerability coverage.
SanerNow platform-datasheet

Many Products, No Security
So many products: Organizations invest in multiple products, many with overlapping
capabilities. And investments are huge when considering the cost of products,maintenance, professional services, training and vendor management.
Many products-no-security

Expensive products with complicated and
overlapping functionality aren’t meeting today’s
security and system management needs.
SanerNow a platform for Endpoint security and systems Management

Endpoint security can be more effective and less costly by simplifying management through a unified platform rather than multiple point products. Currently, organizations invest heavily in numerous security products yet still struggle with attacks, complexity, and high costs. A single platform called SanerNow provides tools to automate tasks like vulnerability management, patching, and threat detection through continuous monitoring from the cloud. It aims to reduce security costs by up to 60% by addressing issues holistically rather than relying on numerous specialized products with overlapping functionality.
Healthcare's Fight Against Ransomware 

Healthcare industry is becoming a popular victim to ransowmare attacks. The following infographic based on some study and statistics depicts the healthcare industry's fight against ransomware.
Take a sneak peek into Saner 2.0

SecPod Saner is an endpoint security solution that provides continuous visibility and control over endpoints. It proactively remediates risks and detects and responds to threats using vulnerability management, patch management, compliance management, and endpoint threat detection and response. Saner allows administrators to gain wide visibility into endpoint activities, create rules to monitor for deviations and fix issues, manage transient devices to keep them protected and up-to-date, create and enforce security compliance policies, and view real-time status reports.
Msp saner 2.0

This document discusses an endpoint security as a service offering that provides continuous endpoint visibility and control. It allows organizations to offer compelling security services by providing visibility into risks, automatically detecting and fixing vulnerabilities in real-time, and ensuring compliance. This increases client revenue through expanded services and introduces new services while also increasing profit margins by maximizing client value and minimizing technical resource costs. The document then introduces a new proactive approach to endpoint security using Saner, which provides real-time endpoint visibility, automatically fixes vulnerabilities and misconfigurations, and detects and responds to threats in seconds through prevention-first capabilities.
Saner 2.0

Saner is an endpoint security solution that provides continuous visibility and control of endpoints. It takes a proactive approach to security by detecting threats and responding before exploits can occur. Saner collects security posture data from endpoints and correlates it with threat intelligence to detect risks and indicators of compromise in real-time. It then automatically fixes vulnerabilities, misconfigurations, and responds to incidents. The solution aims to simplify and automate endpoint security management while reducing costs and ensuring compliance.
Saner 2.0 product sheet

SecPod Saner provides continuous visibility and control for all endpoints. It proactively remediates risks and detects and responds to threats. Saner combines endpoint vulnerability, patch and compliance management with endpoint threat detection and response into one easy to manage solution.
Ransomware - A look back

Ransomware has evolved since its origins in 1989 when the first known "AIDS" trojan spread via floppy disks. There are two main types - locker ransomware that denies access to devices, and crypto ransomware that encrypts files until ransom is paid. Notable examples like Cryptolocker and CryptoLocker have targeted home users, businesses, and public agencies on computers, servers, and mobile devices. Ransomware infects through malicious advertisements, spam emails, downloaders, botnets, and social engineering. Profits from ransomware have grown substantially, reaching over $18 million in 2015. Ransomware impacts many countries worldwide, with payments typically demanded through vouchers or bitcoins.
Worst security data breaches till 2015 - SecPod

The document summarizes major data security breaches from 2006 to 2015. It provides details on the impact and source of each breach. Some key breaches included:
- 2006: Personal information of 26.5 million veterans stolen from a Department of Veterans Affairs database stored on a stolen laptop and hard drive.
- 2007: A Fidelity National Information Services employee stole customer records of 3.2 million people.
- 2013: Hackers gained access to payment card information for up to 110 million Target customers through compromised third-party vendors.
Our talk in Black Hat Asia 2015 Briefing 

In this whitepaper, presented at Black Hat Asia 2015 Briefing session, we highlight how even if the Security Content Automation Protocol (SCAP) federates a number of open standards that are used to enumerate software
flaws and configuration issues related to security, there is a need for having a unique common metadata schema to represent important aspects relevant for designing efficient search engines
Cost Of Cyber Crime

Infographic on the increasing cost of cyber crime and how it affects an organisation.
Choosing The Best AWS Service For Your Website + API.pptx

Have you ever been confused by the myriad of choices offered by AWS for hosting a website or an API?
Lambda, Elastic Beanstalk, Lightsail, Amplify, S3 (and more!) can each host websites + APIs. But which one should we choose?
Which one is cheapest? Which one is fastest? Which one will scale to meet our needs?
Join me in this session as we dive into each AWS hosting service to determine which one is best for your scenario and explain why!
June Patch Tuesday

Ivanti’s Patch Tuesday breakdown goes beyond patching your applications and brings you the intelligence and guidance needed to prioritize where to focus your attention first. Catch early analysis on our Ivanti blog, then join industry expert Chris Goettl for the Patch Tuesday Webinar Event. There we’ll do a deep dive into each of the bulletins and give guidance on the risks associated with the newly-identified vulnerabilities.
More Related Content
More from SecPod Technologies
Hacking Internet of Things (IoT)

The document discusses vulnerabilities in IoT devices and provides examples of potential threats, including hacking a Jeep remotely and changing the target of a smart sniper rifle. It then summarizes challenges in securing IoT devices like limited resources, difficulty upgrading firmware, and lack of security software. Guidelines are provided for vendors, developers, and users to improve IoT security, such as using encryption, patching vulnerabilities, and educating users. Finally, the document demonstrates hacking a DTH set-top box by disturbing service, recording shows without permission, and stealing recordings.
WHY MSSPs LOVE OUR SOLUTION

Managed security service providers (MSSPs) value the Saner Business endpoint security solution for its ability to:
1) Find and eliminate vulnerabilities across networks in an automated and simple way.
2) Offer discrete security services and support regulatory compliance standards through continual assessment and remediation.
3) Provide continuous monitoring and detection of advanced threats that other solutions may overlook.
Many products-no-security (1)

The document discusses the challenges of managing IT security with many individual point products that have overlapping functionality and features. It introduces the SecPod SanerNow platform as a single platform approach for provisioning various security and endpoint management tools on demand to address specific tasks in a simpler and more cost-effective manner. Key benefits highlighted include reducing costs by up to 60%, easing management and improving security through continuous monitoring, vulnerability assessment, and threat detection and response capabilities.
SanerNow Endpoint Management

SanerNow Endpoint Management (EM) is a cloud-delivered
service that allows complete control over all your endpoint
systems. It provides visibility into the status of endpoints and
equips you with hundreds of built-in checks. SanerNow
Endpoint Management provides necessary features for
managing endpoints.
SanerNow Asset Management

SanerNow Asset Management (AM) is a cloud-delivered
service that tracks assets installed on hosts, the open
vulnerabilities in the OS and applications, their patch or update
levels, and prioritizes remediation tasks - all critical to the
deep visibility required to prevent attacks and data breaches.
SanerNow Patch Management

SanerNow Patch Management (PM) is a cloud-delivered
service that identifies and automatically rolls out patches
according to rules and jobs defined by the user. If necessary, it
automatically reboots systems after applying patches and can
roll back installed patches. SanerNow’s patch management
process is timely, responsive and systematically managed.
SanerNow Vulnerability Management

SanerNow Vulnerability Management (VM) is a cloud delivered
service that performs an automated daily vulnerability scan. Organizations can discover their threat and vulnerability risk in less than five minutes. SanerNow VM provides continuous visibility into IT systems. Its time-testedSCAP Feed database delivers comprehensive vulnerability coverage.
SanerNow platform-datasheet

Many Products, No Security
So many products: Organizations invest in multiple products, many with overlapping
capabilities. And investments are huge when considering the cost of products,maintenance, professional services, training and vendor management.
Many products-no-security

Expensive products with complicated and
overlapping functionality aren’t meeting today’s
security and system management needs.
SanerNow a platform for Endpoint security and systems Management

Endpoint security can be more effective and less costly by simplifying management through a unified platform rather than multiple point products. Currently, organizations invest heavily in numerous security products yet still struggle with attacks, complexity, and high costs. A single platform called SanerNow provides tools to automate tasks like vulnerability management, patching, and threat detection through continuous monitoring from the cloud. It aims to reduce security costs by up to 60% by addressing issues holistically rather than relying on numerous specialized products with overlapping functionality.
Healthcare's Fight Against Ransomware 

Healthcare industry is becoming a popular victim to ransowmare attacks. The following infographic based on some study and statistics depicts the healthcare industry's fight against ransomware.
Take a sneak peek into Saner 2.0

SecPod Saner is an endpoint security solution that provides continuous visibility and control over endpoints. It proactively remediates risks and detects and responds to threats using vulnerability management, patch management, compliance management, and endpoint threat detection and response. Saner allows administrators to gain wide visibility into endpoint activities, create rules to monitor for deviations and fix issues, manage transient devices to keep them protected and up-to-date, create and enforce security compliance policies, and view real-time status reports.
Msp saner 2.0

This document discusses an endpoint security as a service offering that provides continuous endpoint visibility and control. It allows organizations to offer compelling security services by providing visibility into risks, automatically detecting and fixing vulnerabilities in real-time, and ensuring compliance. This increases client revenue through expanded services and introduces new services while also increasing profit margins by maximizing client value and minimizing technical resource costs. The document then introduces a new proactive approach to endpoint security using Saner, which provides real-time endpoint visibility, automatically fixes vulnerabilities and misconfigurations, and detects and responds to threats in seconds through prevention-first capabilities.
Saner 2.0

Saner is an endpoint security solution that provides continuous visibility and control of endpoints. It takes a proactive approach to security by detecting threats and responding before exploits can occur. Saner collects security posture data from endpoints and correlates it with threat intelligence to detect risks and indicators of compromise in real-time. It then automatically fixes vulnerabilities, misconfigurations, and responds to incidents. The solution aims to simplify and automate endpoint security management while reducing costs and ensuring compliance.
Saner 2.0 product sheet

SecPod Saner provides continuous visibility and control for all endpoints. It proactively remediates risks and detects and responds to threats. Saner combines endpoint vulnerability, patch and compliance management with endpoint threat detection and response into one easy to manage solution.
Ransomware - A look back

Ransomware has evolved since its origins in 1989 when the first known "AIDS" trojan spread via floppy disks. There are two main types - locker ransomware that denies access to devices, and crypto ransomware that encrypts files until ransom is paid. Notable examples like Cryptolocker and CryptoLocker have targeted home users, businesses, and public agencies on computers, servers, and mobile devices. Ransomware infects through malicious advertisements, spam emails, downloaders, botnets, and social engineering. Profits from ransomware have grown substantially, reaching over $18 million in 2015. Ransomware impacts many countries worldwide, with payments typically demanded through vouchers or bitcoins.
Worst security data breaches till 2015 - SecPod

The document summarizes major data security breaches from 2006 to 2015. It provides details on the impact and source of each breach. Some key breaches included:
- 2006: Personal information of 26.5 million veterans stolen from a Department of Veterans Affairs database stored on a stolen laptop and hard drive.
- 2007: A Fidelity National Information Services employee stole customer records of 3.2 million people.
- 2013: Hackers gained access to payment card information for up to 110 million Target customers through compromised third-party vendors.
Our talk in Black Hat Asia 2015 Briefing 

In this whitepaper, presented at Black Hat Asia 2015 Briefing session, we highlight how even if the Security Content Automation Protocol (SCAP) federates a number of open standards that are used to enumerate software
flaws and configuration issues related to security, there is a need for having a unique common metadata schema to represent important aspects relevant for designing efficient search engines
Cost Of Cyber Crime

Infographic on the increasing cost of cyber crime and how it affects an organisation.
More from SecPod Technologies (20)
SanerNow a platform for Endpoint security and systems Management

SanerNow a platform for Endpoint security and systems Management
Recently uploaded
Choosing The Best AWS Service For Your Website + API.pptx

Have you ever been confused by the myriad of choices offered by AWS for hosting a website or an API?
Lambda, Elastic Beanstalk, Lightsail, Amplify, S3 (and more!) can each host websites + APIs. But which one should we choose?
Which one is cheapest? Which one is fastest? Which one will scale to meet our needs?
Join me in this session as we dive into each AWS hosting service to determine which one is best for your scenario and explain why!
June Patch Tuesday

Ivanti’s Patch Tuesday breakdown goes beyond patching your applications and brings you the intelligence and guidance needed to prioritize where to focus your attention first. Catch early analysis on our Ivanti blog, then join industry expert Chris Goettl for the Patch Tuesday Webinar Event. There we’ll do a deep dive into each of the bulletins and give guidance on the risks associated with the newly-identified vulnerabilities.
Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf

Discover how MongoDB Atlas and vector search technology can revolutionize your application's search capabilities. This comprehensive presentation covers:
* What is Vector Search?
* Importance and benefits of vector search
* Practical use cases across various industries
* Step-by-step implementation guide
* Live demos with code snippets
* Enhancing LLM capabilities with vector search
* Best practices and optimization strategies
Perfect for developers, AI enthusiasts, and tech leaders. Learn how to leverage MongoDB Atlas to deliver highly relevant, context-aware search results, transforming your data retrieval process. Stay ahead in tech innovation and maximize the potential of your applications.
#MongoDB #VectorSearch #AI #SemanticSearch #TechInnovation #DataScience #LLM #MachineLearning #SearchTechnology
Trusted Execution Environment for Decentralized Process Mining

Presentation of the paper "Trusted Execution Environment for Decentralized Process Mining" given during the CAiSE 2024 Conference in Cyprus on June 7, 2024.
Ocean lotus Threat actors project by John Sitima 2024 (1).pptx

Ocean Lotus cyber threat actors represent a sophisticated, persistent, and politically motivated group that poses a significant risk to organizations and individuals in the Southeast Asian region. Their continuous evolution and adaptability underscore the need for robust cybersecurity measures and international cooperation to identify and mitigate the threats posed by such advanced persistent threat groups.
Skybuffer SAM4U tool for SAP license adoption

Manage and optimize your license adoption and consumption with SAM4U, an SAP free customer software asset management tool.
SAM4U, an SAP complimentary software asset management tool for customers, delivers a detailed and well-structured overview of license inventory and usage with a user-friendly interface. We offer a hosted, cost-effective, and performance-optimized SAM4U setup in the Skybuffer Cloud environment. You retain ownership of the system and data, while we manage the ABAP 7.58 infrastructure, ensuring fixed Total Cost of Ownership (TCO) and exceptional services through the SAP Fiori interface.
System Design Case Study: Building a Scalable E-Commerce Platform - Hiike

This case study explores designing a scalable e-commerce platform, covering key requirements, system components, and best practices.
Introduction of Cybersecurity with OSS at Code Europe 2024

I develop the Ruby programming language, RubyGems, and Bundler, which are package managers for Ruby. Today, I will introduce how to enhance the security of your application using open-source software (OSS) examples from Ruby and RubyGems.
The first topic is CVE (Common Vulnerabilities and Exposures). I have published CVEs many times. But what exactly is a CVE? I'll provide a basic understanding of CVEs and explain how to detect and handle vulnerabilities in OSS.
Next, let's discuss package managers. Package managers play a critical role in the OSS ecosystem. I'll explain how to manage library dependencies in your application.
I'll share insights into how the Ruby and RubyGems core team works to keep our ecosystem safe. By the end of this talk, you'll have a better understanding of how to safeguard your code.
Generating privacy-protected synthetic data using Secludy and Milvus

During this demo, the founders of Secludy will demonstrate how their system utilizes Milvus to store and manipulate embeddings for generating privacy-protected synthetic data. Their approach not only maintains the confidentiality of the original data but also enhances the utility and scalability of LLMs under privacy constraints. Attendees, including machine learning engineers, data scientists, and data managers, will witness first-hand how Secludy's integration with Milvus empowers organizations to harness the power of LLMs securely and efficiently.
Energy Efficient Video Encoding for Cloud and Edge Computing Instances

Energy Efficient Video Encoding for Cloud and Edge Computing Instances
A Comprehensive Guide to DeFi Development Services in 2024

DeFi represents a paradigm shift in the financial industry. Instead of relying on traditional, centralized institutions like banks, DeFi leverages blockchain technology to create a decentralized network of financial services. This means that financial transactions can occur directly between parties, without intermediaries, using smart contracts on platforms like Ethereum.
In 2024, we are witnessing an explosion of new DeFi projects and protocols, each pushing the boundaries of what’s possible in finance.
In summary, DeFi in 2024 is not just a trend; it’s a revolution that democratizes finance, enhances security and transparency, and fosters continuous innovation. As we proceed through this presentation, we'll explore the various components and services of DeFi in detail, shedding light on how they are transforming the financial landscape.
At Intelisync, we specialize in providing comprehensive DeFi development services tailored to meet the unique needs of our clients. From smart contract development to dApp creation and security audits, we ensure that your DeFi project is built with innovation, security, and scalability in mind. Trust Intelisync to guide you through the intricate landscape of decentralized finance and unlock the full potential of blockchain technology.
Ready to take your DeFi project to the next level? Partner with Intelisync for expert DeFi development services today!
TrustArc Webinar - 2024 Global Privacy Survey

How does your privacy program stack up against your peers? What challenges are privacy teams tackling and prioritizing in 2024?
In the fifth annual Global Privacy Benchmarks Survey, we asked over 1,800 global privacy professionals and business executives to share their perspectives on the current state of privacy inside and outside of their organizations. This year’s report focused on emerging areas of importance for privacy and compliance professionals, including considerations and implications of Artificial Intelligence (AI) technologies, building brand trust, and different approaches for achieving higher privacy competence scores.
See how organizational priorities and strategic approaches to data security and privacy are evolving around the globe.
This webinar will review:
- The top 10 privacy insights from the fifth annual Global Privacy Benchmarks Survey
- The top challenges for privacy leaders, practitioners, and organizations in 2024
- Key themes to consider in developing and maintaining your privacy program
Fueling AI with Great Data with Airbyte Webinar

This talk will focus on how to collect data from a variety of sources, leveraging this data for RAG and other GenAI use cases, and finally charting your course to productionalization.
Azure API Management to expose backend services securely

How to use Azure API Management to expose backend service securely
Finale of the Year: Apply for Next One!

Presentation for the event called "Finale of the Year: Apply for Next One!" organized by GDSC PJATK
Recently uploaded (20)
Choosing The Best AWS Service For Your Website + API.pptx

Choosing The Best AWS Service For Your Website + API.pptx
Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf

Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf
Trusted Execution Environment for Decentralized Process Mining

Trusted Execution Environment for Decentralized Process Mining
Ocean lotus Threat actors project by John Sitima 2024 (1).pptx

Ocean lotus Threat actors project by John Sitima 2024 (1).pptx
System Design Case Study: Building a Scalable E-Commerce Platform - Hiike

System Design Case Study: Building a Scalable E-Commerce Platform - Hiike
Introduction of Cybersecurity with OSS at Code Europe 2024

Introduction of Cybersecurity with OSS at Code Europe 2024
Generating privacy-protected synthetic data using Secludy and Milvus

Generating privacy-protected synthetic data using Secludy and Milvus
Energy Efficient Video Encoding for Cloud and Edge Computing Instances

Energy Efficient Video Encoding for Cloud and Edge Computing Instances
Deep Dive: AI-Powered Marketing to Get More Leads and Customers with HyperGro...

Deep Dive: AI-Powered Marketing to Get More Leads and Customers with HyperGro...
Overcoming the PLG Trap: Lessons from Canva's Head of Sales & Head of EMEA Da...

Overcoming the PLG Trap: Lessons from Canva's Head of Sales & Head of EMEA Da...
A Comprehensive Guide to DeFi Development Services in 2024

A Comprehensive Guide to DeFi Development Services in 2024
Nordic Marketo Engage User Group_June 13_ 2024.pptx

Nordic Marketo Engage User Group_June 13_ 2024.pptx
WeTestAthens: Postman's AI & Automation Techniques

WeTestAthens: Postman's AI & Automation Techniques
Azure API Management to expose backend services securely

Azure API Management to expose backend services securely
