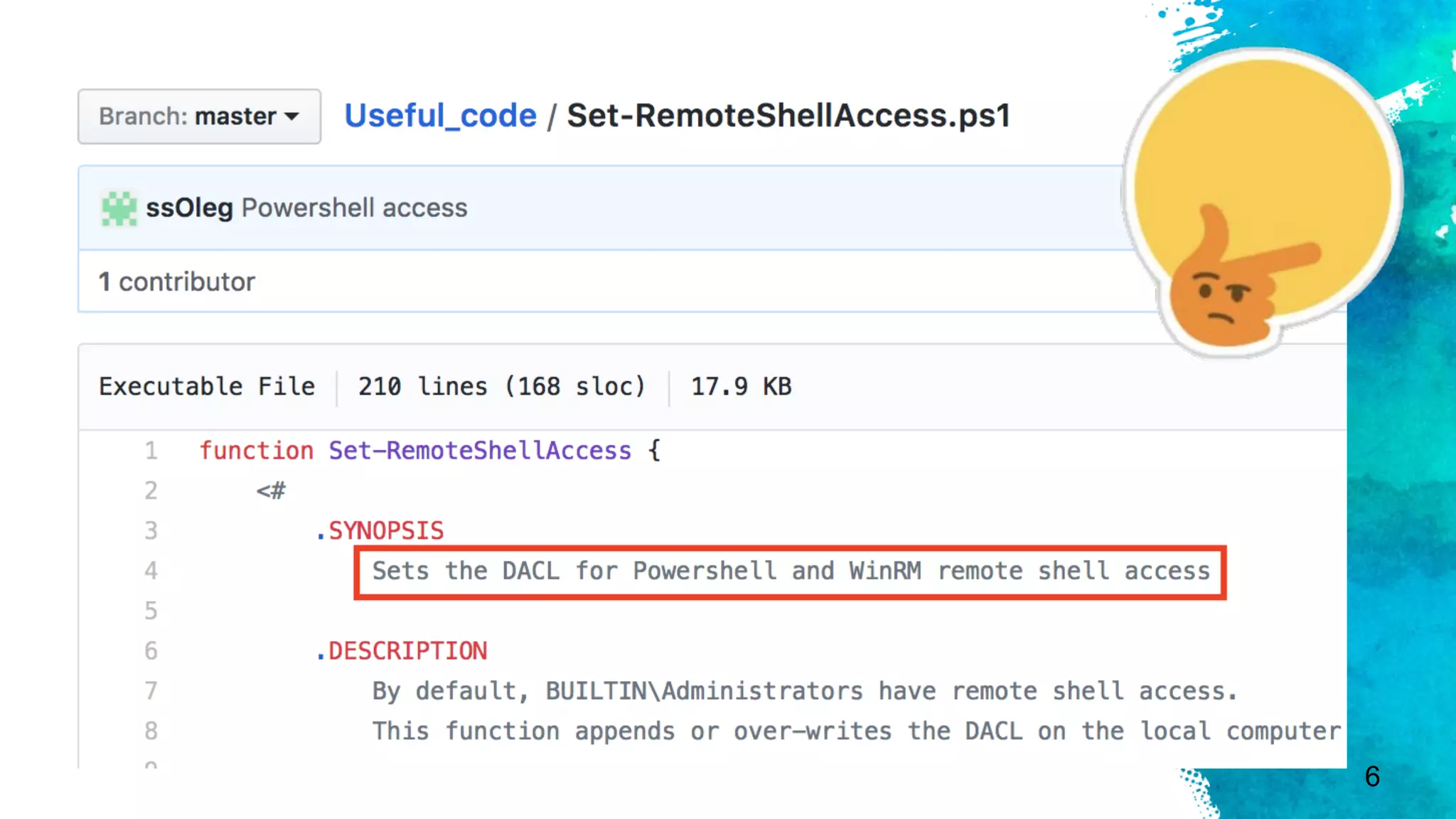
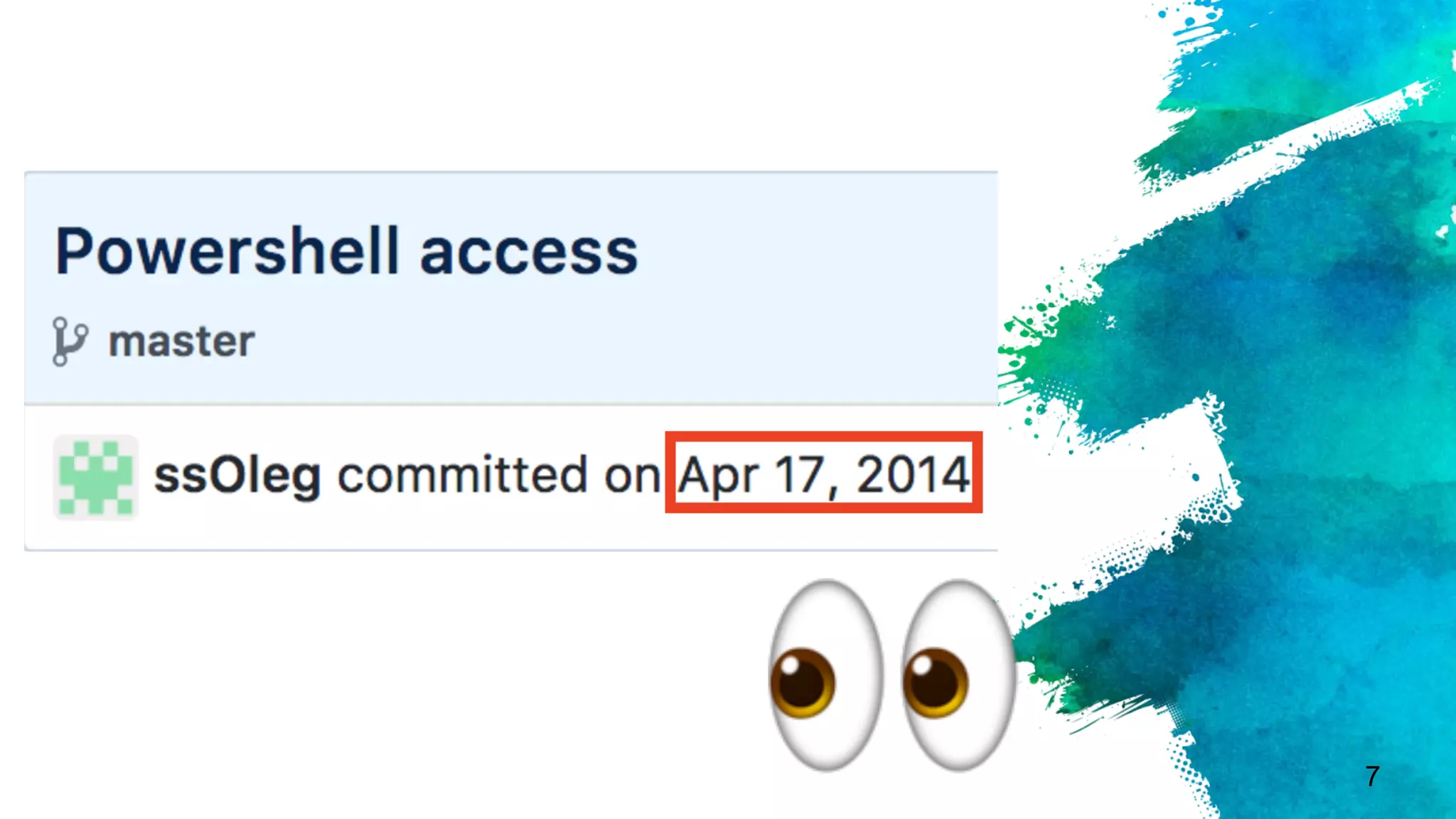
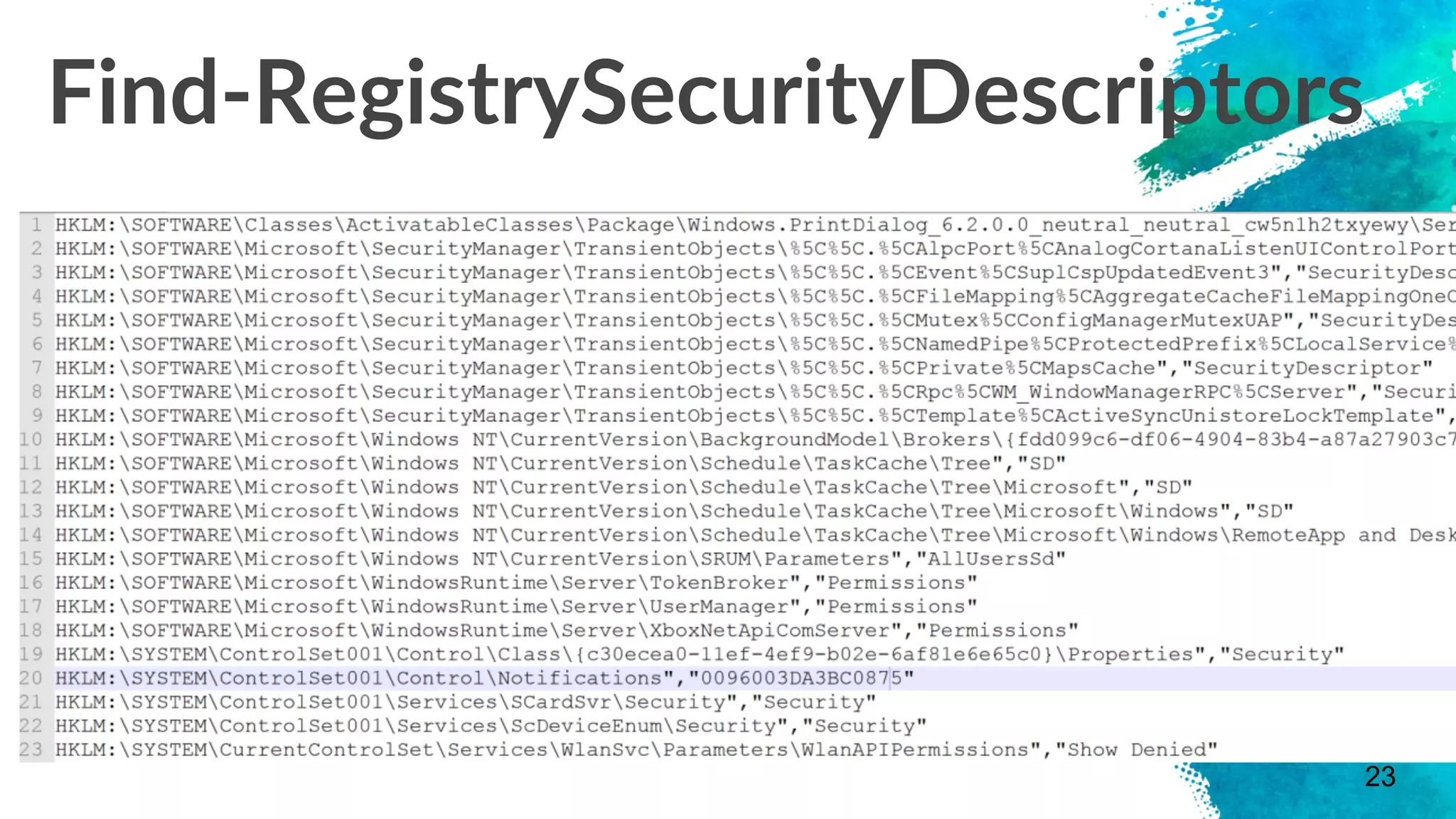
The document discusses stealthy host persistence techniques using security descriptors. It begins with an introduction to the authors and their research focusing on offensive applications of securable objects. It then provides an overview of securable objects, access control lists, and the authors' methodology for researching new persistence primitives using various securable objects like the Service Control Manager, WinRM, DCOM, WMI namespaces, printers, and the remote registry. Case studies and demonstrations are presented for some of these objects.































![Remote Registry
× Allows permitted users/groups to access the
registry remotely via .NET/Win32 API
× [Microsoft.Win32.RegistryKey]::OpenRemoteBaseKey()
× The RemoteRegistry service has to be enabled
and the calling user has to have access
× By default in Windows 7/10, this service is
disabled
× Remote access to the registry == ability to
dump hashes (among other things) 😈
51](https://image.slidesharecdn.com/anaceinthehole-stealthyhostpersistenceviasecuritydescriptors-170925230421/75/An-ACE-in-the-Hole-Stealthy-Host-Persistence-via-Security-Descriptors-51-2048.jpg)