What really happens when you lose your phone? - Symantec
•
0 likes•498 views
A national experiment explores the risks your smartphone and private data face daily.
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
More Related Content
Similar to What really happens when you lose your phone? - Symantec
Similar to What really happens when you lose your phone? - Symantec (20)
WCC 2012: General security introduction for non-security students

WCC 2012: General security introduction for non-security students
How to Secure Your iOs Device and Keep Client Data Safe

How to Secure Your iOs Device and Keep Client Data Safe
National Life IT Department's Cyber Security Awareness Presentation

National Life IT Department's Cyber Security Awareness Presentation
More from Cheapest SSLs
More from Cheapest SSLs (15)
Four ways to secure the internet of things - infographic

Four ways to secure the internet of things - infographic
Beware Of More Targeted Attacks And Data Breaches - Infographic

Beware Of More Targeted Attacks And Data Breaches - Infographic
Why private browsing doesn't exist and how to fix it

Why private browsing doesn't exist and how to fix it
Business Critical SSL Certificate Management - Infographic

Business Critical SSL Certificate Management - Infographic
12 Tips To Boost Trust & Conversions This Christmas with Thawte

12 Tips To Boost Trust & Conversions This Christmas with Thawte
Protect data in transit across your business and around the world

Protect data in transit across your business and around the world
How attackers hack atm & withdraw cash from an atm using a phone - Infographic

How attackers hack atm & withdraw cash from an atm using a phone - Infographic
Recently uploaded
TEST BANK For Principles of Anatomy and Physiology, 16th Edition by Gerard J. Tortora, Verified Chapters 1 - 29, Complete Newest Version.TEST BANK For Principles of Anatomy and Physiology, 16th Edition by Gerard J....

TEST BANK For Principles of Anatomy and Physiology, 16th Edition by Gerard J....rightmanforbloodline
Recently uploaded (20)
TEST BANK For Principles of Anatomy and Physiology, 16th Edition by Gerard J....

TEST BANK For Principles of Anatomy and Physiology, 16th Edition by Gerard J....
Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...

Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...
"I see eyes in my soup": How Delivery Hero implemented the safety system for ...

"I see eyes in my soup": How Delivery Hero implemented the safety system for ...
Connector Corner: Accelerate revenue generation using UiPath API-centric busi...

Connector Corner: Accelerate revenue generation using UiPath API-centric busi...
DEV meet-up UiPath Document Understanding May 7 2024 Amsterdam

DEV meet-up UiPath Document Understanding May 7 2024 Amsterdam
Choreo: Empowering the Future of Enterprise Software Engineering

Choreo: Empowering the Future of Enterprise Software Engineering
Introduction to Multilingual Retrieval Augmented Generation (RAG)

Introduction to Multilingual Retrieval Augmented Generation (RAG)
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
The Zero-ETL Approach: Enhancing Data Agility and Insight

The Zero-ETL Approach: Enhancing Data Agility and Insight
Vector Search -An Introduction in Oracle Database 23ai.pptx

Vector Search -An Introduction in Oracle Database 23ai.pptx
What really happens when you lose your phone? - Symantec
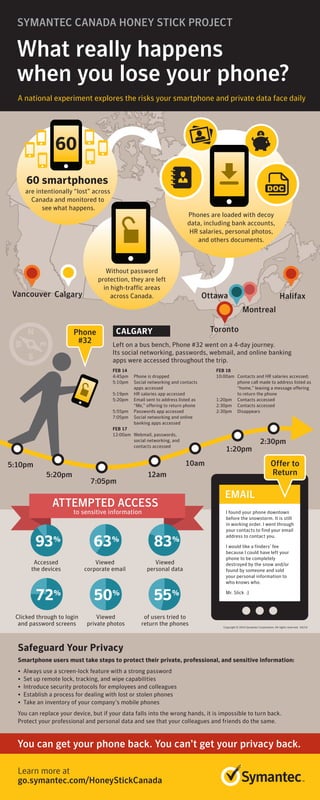
- 1. Vancouver Calgary Ottawa Toronto Montreal Halifax What really happens when you lose your phone? Learn more at go.symantec.com/HoneyStickCanada Safeguard Your Privacy Smartphone users must take steps to protect their private, professional, and sensitive information: • Always use a screen-lock feature with a strong password • Set up remote lock, tracking, and wipe capabilities • Introduce security protocols for employees and colleagues • Establish a process for dealing with lost or stolen phones • Take an inventory of your company’s mobile phones You can replace your device, but if your data falls into the wrong hands, it is impossible to turn back. Protect your professional and personal data and see that your colleagues and friends do the same. You can get your phone back. You can’t get your privacy back. A national experiment explores the risks your smartphone and private data face daily SYMANTEC CANADA HONEY STICK PROJECT I found your phone downtown before the snowstorm. It is still in working order. I went through your contacts to find your email address to contact you. I would like a finders’ fee because I could have left your phone to be completely destroyed by the snow and/or found by someone and sold your personal information to who knows who. Mr. Slick :) EMAIL Phone #32 Offer to Return Copyright © 2014 Symantec Corporation. All rights reserved. 04/14 ATTEMPTED ACCESS 93% 63% 83% 72% 50% Accessed the devices to sensitive information Clicked through to login and password screens Viewed corporate email Viewed personal data Viewed private photos of users tried to return the phones 55% Left on a bus bench, Phone #32 went on a 4-day journey. Its social networking, passwords, webmail, and online banking apps were accessed throughout the trip. CALGARY FEB 14 4:45pm Phone is dropped 5:10pm Social networking and contacts apps accessed 5:19pm HR salaries app accessed 5:20pm Email sent to address listed as “Me,” offering to return phone 5:55pm Passwords app accessed 7:05pm Social networking and online banking apps accessed FEB 17 12:00am Webmail, passwords, social networking, and contacts accessed FEB 18 10:00am Contacts and HR salaries accessed; phone call made to address listed as “home,” leaving a message offering to return the phone 1:20pm Contacts accessed 2:30pm Contacts accessed 2:30pm Disappears 5:10pm 5:20pm 7:05pm 12am 10am 1:20pm 2:30pm Without password protection, they are left in high-traffic areas across Canada. Phones are loaded with decoy data, including bank accounts, HR salaries, personal photos, and others documents. 60 smartphones 60 are intentionally “lost” across Canada and monitored to see what happens.
