Infraguard Access Management
•
0 likes•9 views
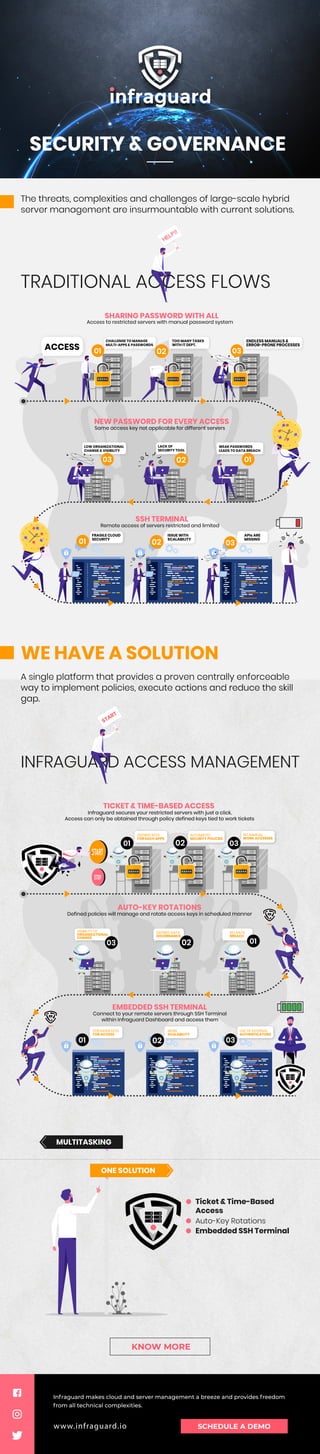
A single platform that provides a proven centrally enforceable way to implement policies, execute actions and reduce the skill gap.
Report
Share
Report
Share
Download to read offline
Recommended
Advanced Privileged Identity Management: Moving Beyond the Gateway Approach t...

Advanced Privileged Identity Management: Moving Beyond the Gateway Approach t...SSH Communications Security
More Related Content
Similar to Infraguard Access Management
Advanced Privileged Identity Management: Moving Beyond the Gateway Approach t...

Advanced Privileged Identity Management: Moving Beyond the Gateway Approach t...SSH Communications Security
Similar to Infraguard Access Management (20)
Securing Digital Identities and Transactions in the Cloud Security Guide

Securing Digital Identities and Transactions in the Cloud Security Guide
Advanced Privileged Identity Management: Moving Beyond the Gateway Approach t...

Advanced Privileged Identity Management: Moving Beyond the Gateway Approach t...
RETOS ACTUALES E INNOVACIÓN SOBRE EL CONTROL DE ACCESOS PRIVILEGIADOS.

RETOS ACTUALES E INNOVACIÓN SOBRE EL CONTROL DE ACCESOS PRIVILEGIADOS.
#MFSummit2016 Secure: Is your mainframe less secure than your fileserver

#MFSummit2016 Secure: Is your mainframe less secure than your fileserver
SafeWord 2008 Migration Bundle Building a Fully Trusted Authentication Enviro...

SafeWord 2008 Migration Bundle Building a Fully Trusted Authentication Enviro...
Recently uploaded
Hot Sexy call girls in Patel Nagar🔝 9953056974 🔝 escort Service

Hot Sexy call girls in Patel Nagar🔝 9953056974 🔝 escort Service9953056974 Low Rate Call Girls In Saket, Delhi NCR
Recently uploaded (20)
Dealing with Cultural Dispersion — Stefano Lambiase — ICSE-SEIS 2024

Dealing with Cultural Dispersion — Stefano Lambiase — ICSE-SEIS 2024
Balasore Best It Company|| Top 10 IT Company || Balasore Software company Odisha

Balasore Best It Company|| Top 10 IT Company || Balasore Software company Odisha
Catch the Wave: SAP Event-Driven and Data Streaming for the Intelligence Ente...

Catch the Wave: SAP Event-Driven and Data Streaming for the Intelligence Ente...
Maximizing Efficiency and Profitability with OnePlan’s Professional Service A...

Maximizing Efficiency and Profitability with OnePlan’s Professional Service A...
Automate your Kamailio Test Calls - Kamailio World 2024

Automate your Kamailio Test Calls - Kamailio World 2024
Simplifying Microservices & Apps - The art of effortless development - Meetup...

Simplifying Microservices & Apps - The art of effortless development - Meetup...
Comparing Linux OS Image Update Models - EOSS 2024.pdf

Comparing Linux OS Image Update Models - EOSS 2024.pdf
Unveiling Design Patterns: A Visual Guide with UML Diagrams

Unveiling Design Patterns: A Visual Guide with UML Diagrams
What is Advanced Excel and what are some best practices for designing and cre...

What is Advanced Excel and what are some best practices for designing and cre...
Alfresco TTL#157 - Troubleshooting Made Easy: Deciphering Alfresco mTLS Confi...

Alfresco TTL#157 - Troubleshooting Made Easy: Deciphering Alfresco mTLS Confi...
Machine Learning Software Engineering Patterns and Their Engineering

Machine Learning Software Engineering Patterns and Their Engineering
Hot Sexy call girls in Patel Nagar🔝 9953056974 🔝 escort Service

Hot Sexy call girls in Patel Nagar🔝 9953056974 🔝 escort Service
Infraguard Access Management
- 1. ACCESS Same access key not applicable for different servers Access to restricted servers with manual password system NEW PASSWORD FOR EVERY ACCESS SHARING PASSWORD WITH ALL Remote access of servers restricted and limited SSH TERMINAL Defined policies will manage and rotate access keys in scheduled manner Infraguard secures your restricted servers with just a click. Access can only be obtained through policy defined keys tied to work tickets TICKET & TIME-BASED ACCESS AUTO-KEY ROTATIONS Connect to your remote servers through SSH Terminal within Infraguard Dashboard and access them EMBEDDED SSH TERMINAL Ticket & Time-Based Access Auto-Key Rotations Embedded SSH Terminal 01 02 SECURITY & GOVERNANCE TRADITIONAL ACCESS FLOWS INFRAGUARD ACCESS MANAGEMENT START 03 MULTITASKING ONE SOLUTION 01 DEFINED KEYS FOR EACH APPS 03 NO MANUAL WORK ACCESSES 02 AUTOMATED SECURITY POLICIES LACK OF SECURITY TOOL LOW ORGANIZATIONAL CHANGE & VISIBILITY VISIBILITY OF ORGANIZATIONAL CHANGE 02 01 03 FRAGILE CLOUD SECURITY 01 02 03 03 01 02 03 The threats, complexities and challenges of large-scale hybrid server management are insurmountable with current solutions. WE HAVE A SOLUTION A single platform that provides a proven centrally enforceable way to implement policies, execute actions and reduce the skill gap. Infraguard makes cloud and server management a breeze and provides freedom from all technical complexities. SCHEDULE A DEMO www.infraguard.io KNOW MORE TOO MANY TASKS WITH IT DEPT. ISSUE WITH SCALABILITY APIs ARE MISSING DEFINED DATA GOVERNANCE NO DATA BREACH 01 02 STRONGER KEYS FOR ACCESS MORE SCALABILITY USE OF EXTERNAL AUTHENTICATORS CHALLENGE TO MANAGE MULTI-APPS & PASSWORDS ENDLESS MANUALS & ERROR-PRONE PROCESSES WEAK PASSWORDS LEADS TO DATA BREACH
