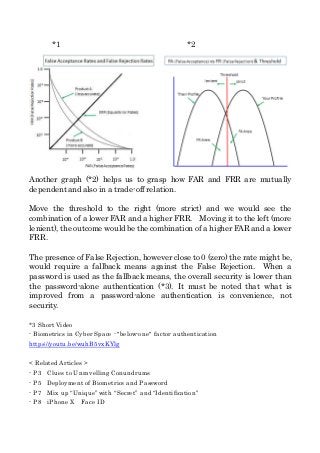
FAR and FRR are not just mutually dependent but are in a trade-off relation. The level of a FAR that rejects a twin would have to bring the level of a FRR that rejects the registered user very frequently. The level of a FRR that eliminates the need of a fallback means would have to bring the level of a FAR that accepts nearly anyone.
< Videos >
Turn off biometrics where security matters (30 seconds)
https://youtu.be/7UAgtPtmUbk
Biometrics in Cyber Space - "below-one" factor authentication
https://youtu.be/wuhB5vxKYlg
Six Reasons to Believe Biometrics Don't Ruin Cyber Security
https://youtu.be/lODTiO2k8ws
Password-free Life - Utopia or Dystopia? (30 seconds)
https://youtu.be/UJDBZpX1a0U
Password Predicament and Expanded Password System
https://youtu.be/-KEE2VdDnY0