Securing Dynamic Cloud Environments
•
0 likes•234 views
Digital transformation is driving heterogenous cloud adoption within the enterprise, including: Private cloud — ongoing data center evolution with virtualization, software-defined networking (SDN), software-defined data center (SDDC) Public and hybrid cloud — cloud migration with AWS, Microsoft Azure, or other Infrastructure-as-a-Service (IaaS) providers Software as a Service (SaaS) applications — Office 365, Salesforce, etc. At the same time, concerns about security, privacy, and compliance have remained key cloud adoption and migration issues. Addressing these requires a multi-cloud security approach that can mitigate the risk of the expanded attack surface across both on-premises and multiple IaaS and SaaS environments.
Report
Share
Report
Share
Download to read offline
Recommended
More Related Content
More from Fortinet
More from Fortinet (6)
Infographic: Bringing Your Cloud Visibility Back Into Focus

Infographic: Bringing Your Cloud Visibility Back Into Focus
Infographic: Fortinet Q1 2017 Threat Landscape Report

Infographic: Fortinet Q1 2017 Threat Landscape Report
Recently uploaded
Recently uploaded (20)
Digital Identity is Under Attack: FIDO Paris Seminar.pptx

Digital Identity is Under Attack: FIDO Paris Seminar.pptx
Genislab builds better products and faster go-to-market with Lean project man...

Genislab builds better products and faster go-to-market with Lean project man...
A Journey Into the Emotions of Software Developers

A Journey Into the Emotions of Software Developers
Merck Moving Beyond Passwords: FIDO Paris Seminar.pptx

Merck Moving Beyond Passwords: FIDO Paris Seminar.pptx
TeamStation AI System Report LATAM IT Salaries 2024

TeamStation AI System Report LATAM IT Salaries 2024
Generative Artificial Intelligence: How generative AI works.pdf

Generative Artificial Intelligence: How generative AI works.pdf
The Future Roadmap for the Composable Data Stack - Wes McKinney - Data Counci...

The Future Roadmap for the Composable Data Stack - Wes McKinney - Data Counci...
Arizona Broadband Policy Past, Present, and Future Presentation 3/25/24

Arizona Broadband Policy Past, Present, and Future Presentation 3/25/24
Emixa Mendix Meetup 11 April 2024 about Mendix Native development

Emixa Mendix Meetup 11 April 2024 about Mendix Native development
Potential of AI (Generative AI) in Business: Learnings and Insights

Potential of AI (Generative AI) in Business: Learnings and Insights
Decarbonising Buildings: Making a net-zero built environment a reality

Decarbonising Buildings: Making a net-zero built environment a reality
Testing tools and AI - ideas what to try with some tool examples

Testing tools and AI - ideas what to try with some tool examples
Assure Ecommerce and Retail Operations Uptime with ThousandEyes

Assure Ecommerce and Retail Operations Uptime with ThousandEyes
[Webinar] SpiraTest - Setting New Standards in Quality Assurance![[Webinar] SpiraTest - Setting New Standards in Quality Assurance](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Webinar] SpiraTest - Setting New Standards in Quality Assurance](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Webinar] SpiraTest - Setting New Standards in Quality Assurance
Transcript: New from BookNet Canada for 2024: Loan Stars - Tech Forum 2024

Transcript: New from BookNet Canada for 2024: Loan Stars - Tech Forum 2024
UiPath Community: Communication Mining from Zero to Hero

UiPath Community: Communication Mining from Zero to Hero
Securing Dynamic Cloud Environments
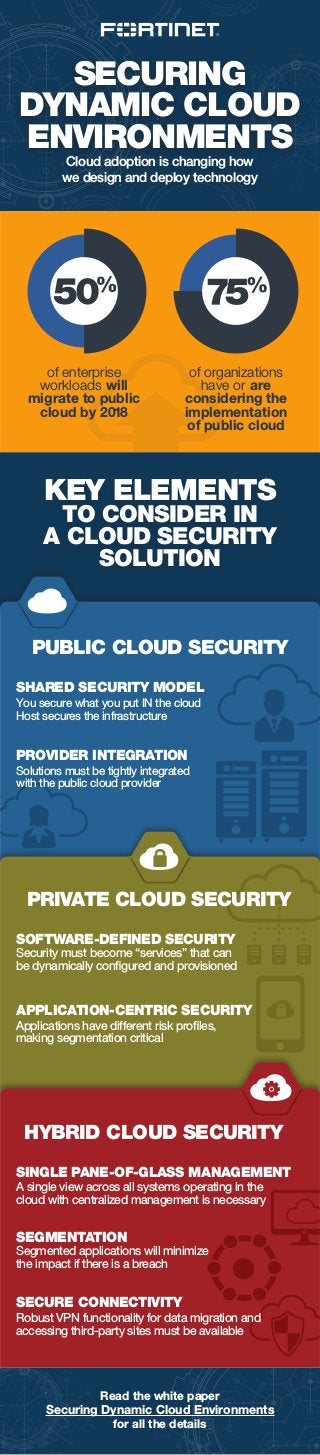
- 1. SECURING DYNAMIC CLOUD ENVIRONMENTS Cloud adoption is changing how we design and deploy technology Read the white paper Securing Dynamic Cloud Environments for all the details SHARED SECURITY MODEL You secure what you put IN the cloud Host secures the infrastructure Security must become “services” that can be dynamically configured and provisioned SOFTWARE-DEFINED SECURITY PUBLIC CLOUD SECURITY of enterprise workloads will migrate to public cloud by 2018 of organizations have or are considering the implementation of public cloud KEY ELEMENTS TO CONSIDER IN A CLOUD SECURITY SOLUTION Applications have different risk profiles, making segmentation critical APPLICATION-CENTRIC SECURITY Solutions must be tightly integrated with the public cloud provider PROVIDER INTEGRATION PRIVATE CLOUD SECURITY HYBRID CLOUD SECURITY Robust VPN functionality for data migration and accessing third-party sites must be available SECURE CONNECTIVITY Segmented applications will minimize the impact if there is a breach SEGMENTATION A single view across all systems operating in the cloud with centralized management is necessary SINGLE PANE-OF-GLASS MANAGEMENT
