Recommended
More Related Content
What's hot
What's hot (20)
12 Things Every Woman Wants to Tell Her Mother-in-Law

12 Things Every Woman Wants to Tell Her Mother-in-Law
12 Things Every Woman Wants to Tell Her Mother-in-Law

12 Things Every Woman Wants to Tell Her Mother-in-Law
Prilog:Kviz „Daj svoj online doprinos“ s analizom odgovora 

Prilog:Kviz „Daj svoj online doprinos“ s analizom odgovora
Sr. master tracy lee thomas, martial arts master in virginia beach

Sr. master tracy lee thomas, martial arts master in virginia beach
Cyber safety: internet safety presentation for middle school students

Cyber safety: internet safety presentation for middle school students
How family law lawyers and clients can avoid social media dangers: 30 Tips in...

How family law lawyers and clients can avoid social media dangers: 30 Tips in...
Viewers also liked
Viewers also liked (7)
Similar to Handout
Similar to Handout (20)
Internet do's and don'ts. Kids safety on the Internet 

Internet do's and don'ts. Kids safety on the Internet
Social Media Training for Parents: Keeping Your Kids Safe Online

Social Media Training for Parents: Keeping Your Kids Safe Online
Recently uploaded
Recently uploaded (20)
Infrared simulation and processing on Nvidia platforms

Infrared simulation and processing on Nvidia platforms
WomenInAutomation2024: AI and Automation for eveyone

WomenInAutomation2024: AI and Automation for eveyone
React Native vs Ionic - The Best Mobile App Framework

React Native vs Ionic - The Best Mobile App Framework
Generative AI - Gitex v1Generative AI - Gitex v1.pptx

Generative AI - Gitex v1Generative AI - Gitex v1.pptx
How to Effectively Monitor SD-WAN and SASE Environments with ThousandEyes

How to Effectively Monitor SD-WAN and SASE Environments with ThousandEyes
Generative Artificial Intelligence: How generative AI works.pdf

Generative Artificial Intelligence: How generative AI works.pdf
How Tech Giants Cut Corners to Harvest Data for A.I.

How Tech Giants Cut Corners to Harvest Data for A.I.
Long journey of Ruby standard library at RubyConf AU 2024

Long journey of Ruby standard library at RubyConf AU 2024
Glenn Lazarus- Why Your Observability Strategy Needs Security Observability

Glenn Lazarus- Why Your Observability Strategy Needs Security Observability
Bridging Between CAD & GIS: 6 Ways to Automate Your Data Integration

Bridging Between CAD & GIS: 6 Ways to Automate Your Data Integration
Decarbonising Buildings: Making a net-zero built environment a reality

Decarbonising Buildings: Making a net-zero built environment a reality
Emixa Mendix Meetup 11 April 2024 about Mendix Native development

Emixa Mendix Meetup 11 April 2024 about Mendix Native development
Why device, WIFI, and ISP insights are crucial to supporting remote Microsoft...

Why device, WIFI, and ISP insights are crucial to supporting remote Microsoft...
Handout
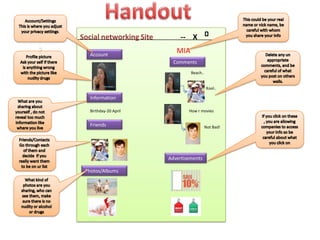
- 1. Handout This could be your real name or nick name, be careful with whom you share your info Account/Settings This is where you adjust your privacy settings. ? Social networking Site -- X MIA Account Profile picture Ask your self if there is anything wrong with the picture like nudity drugs Delete any un appropriate comments, and be careful of what you post on others walls. Comments Beach.. Kool.. Information What are you sharing about yourself , do not reveal too much information like where you live Birthday-20 April How r movies If you click on these , you are allowing companies to access your info so be careful about what you click on Friends Not Bad! Friends/Contacts Go through each of them and decide if you really want them to be on ur list Advertisements Photos/Albums What kind of photos are you sharing, who can see them, make sure there is no nudity or alcohol or drugs
- 3. Always tell a parent or teacher if you see any bad language or pictures on the Internet, or if anyone writes anything you don’t like.
- 4. Do not reply to any messages or bulletin board items that are suggestive, obscene, aggressive, or distressing.
- 5. Do not use bad language online, neither will you take part in arguments or fights online.
- 6. Do not accept any offers of money or presents, even free offers.
- 7. Do not order anything online or give out credit card details.
- 8. Do not enter chat rooms and websites that you have agreed with your parents as off-limits.
- 9. Do not arrange any face-to-face meetings with anyone you have met on the Internet unless your parents consent and they accompany you.