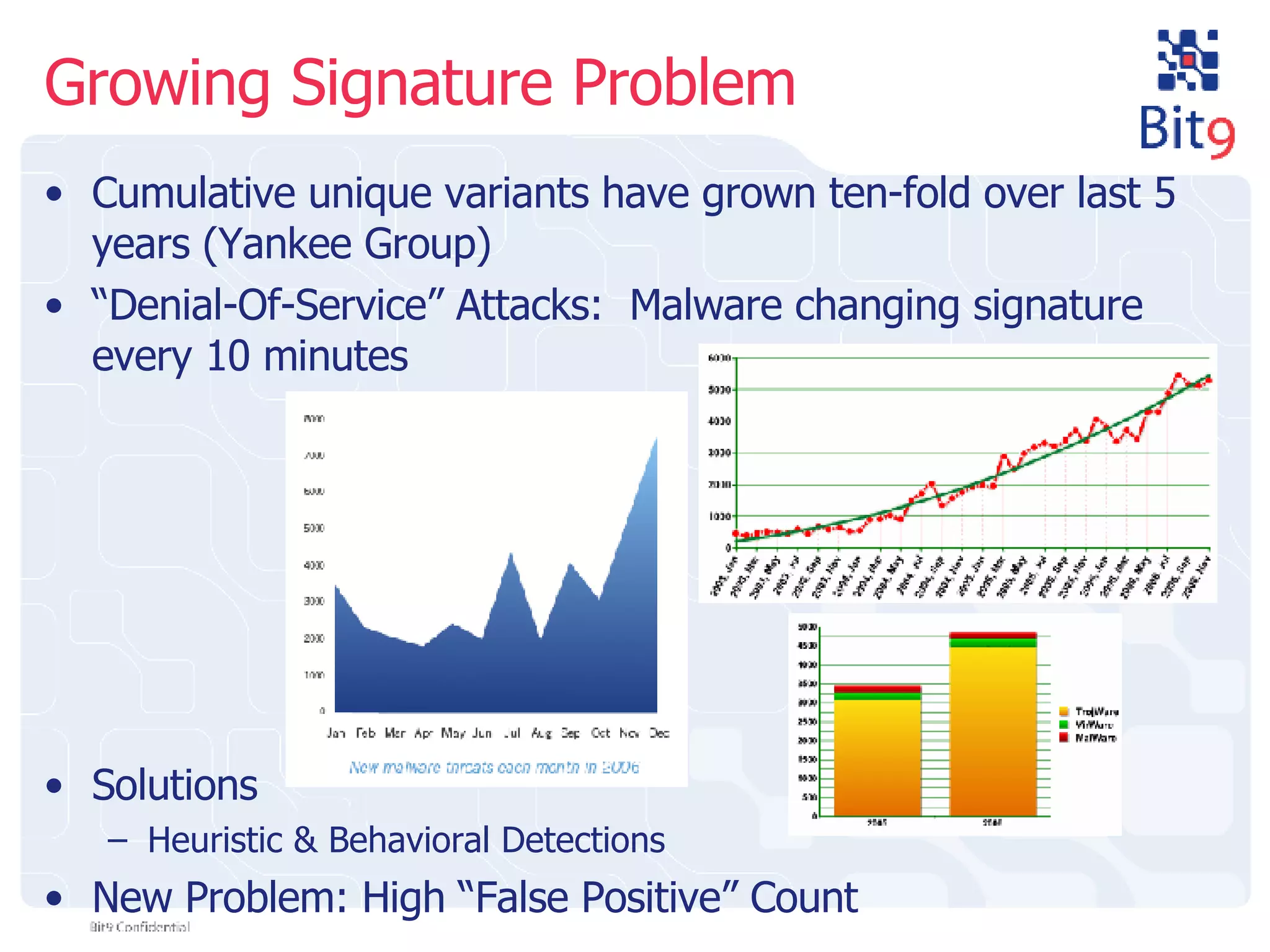
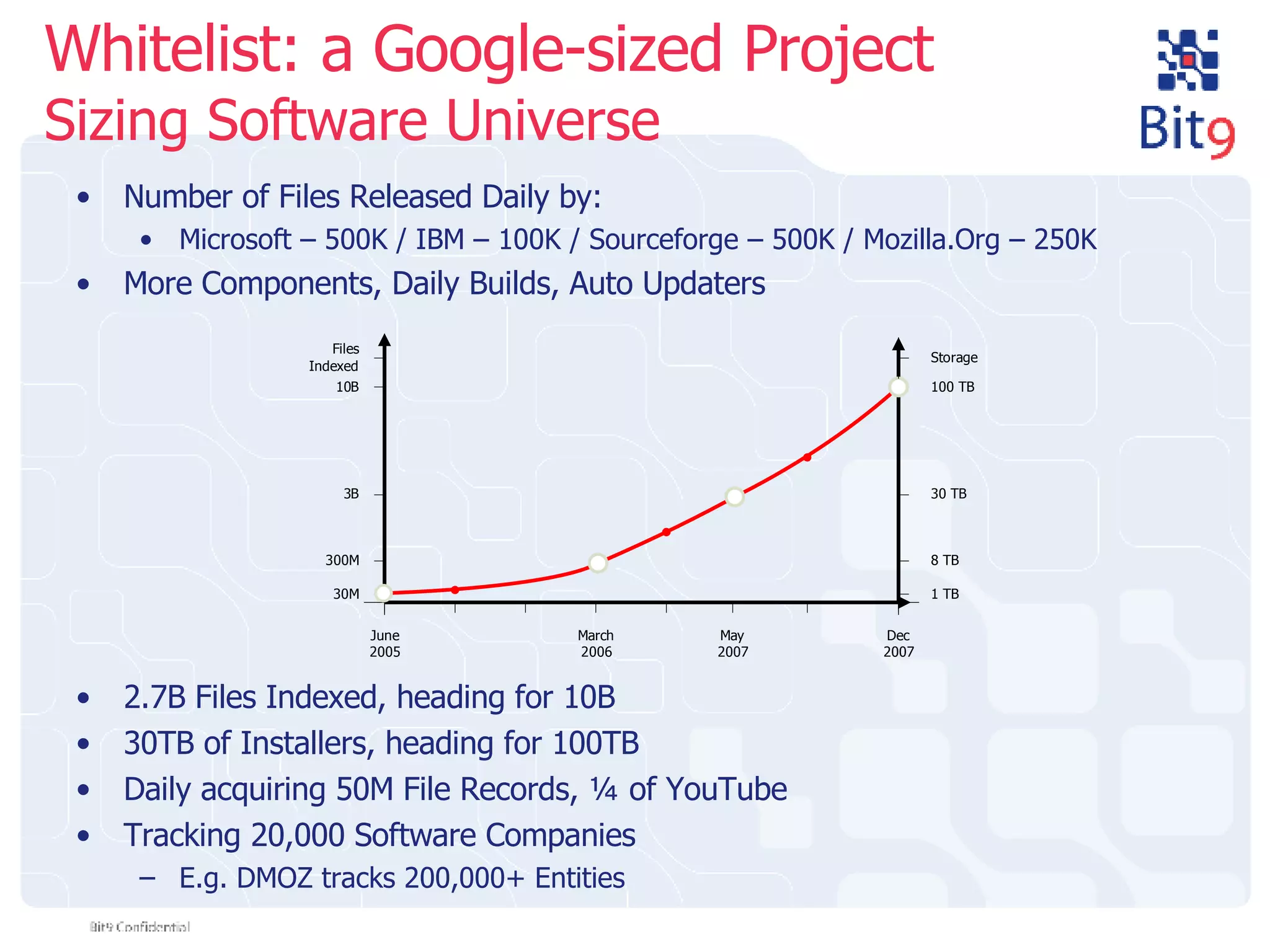
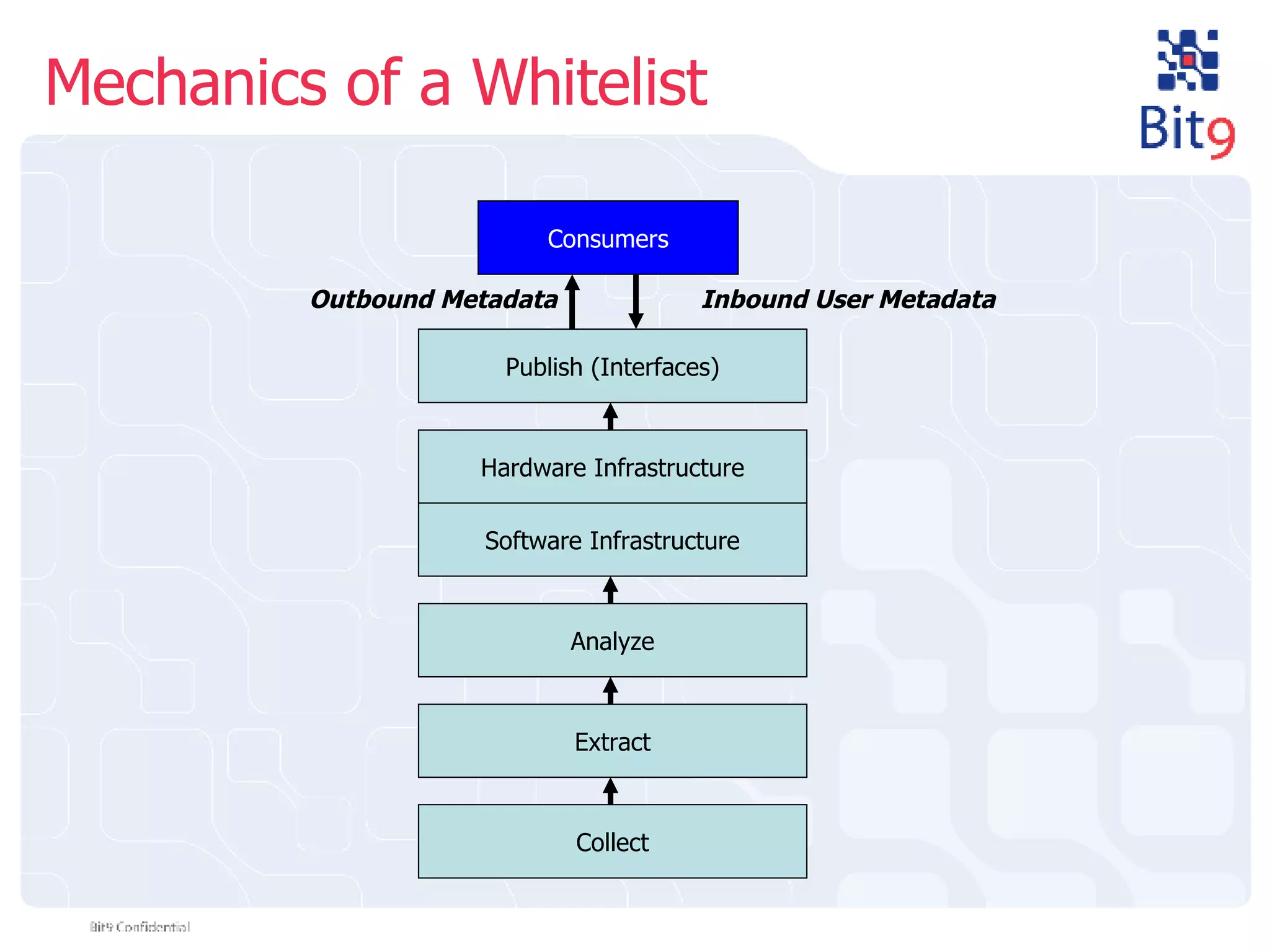
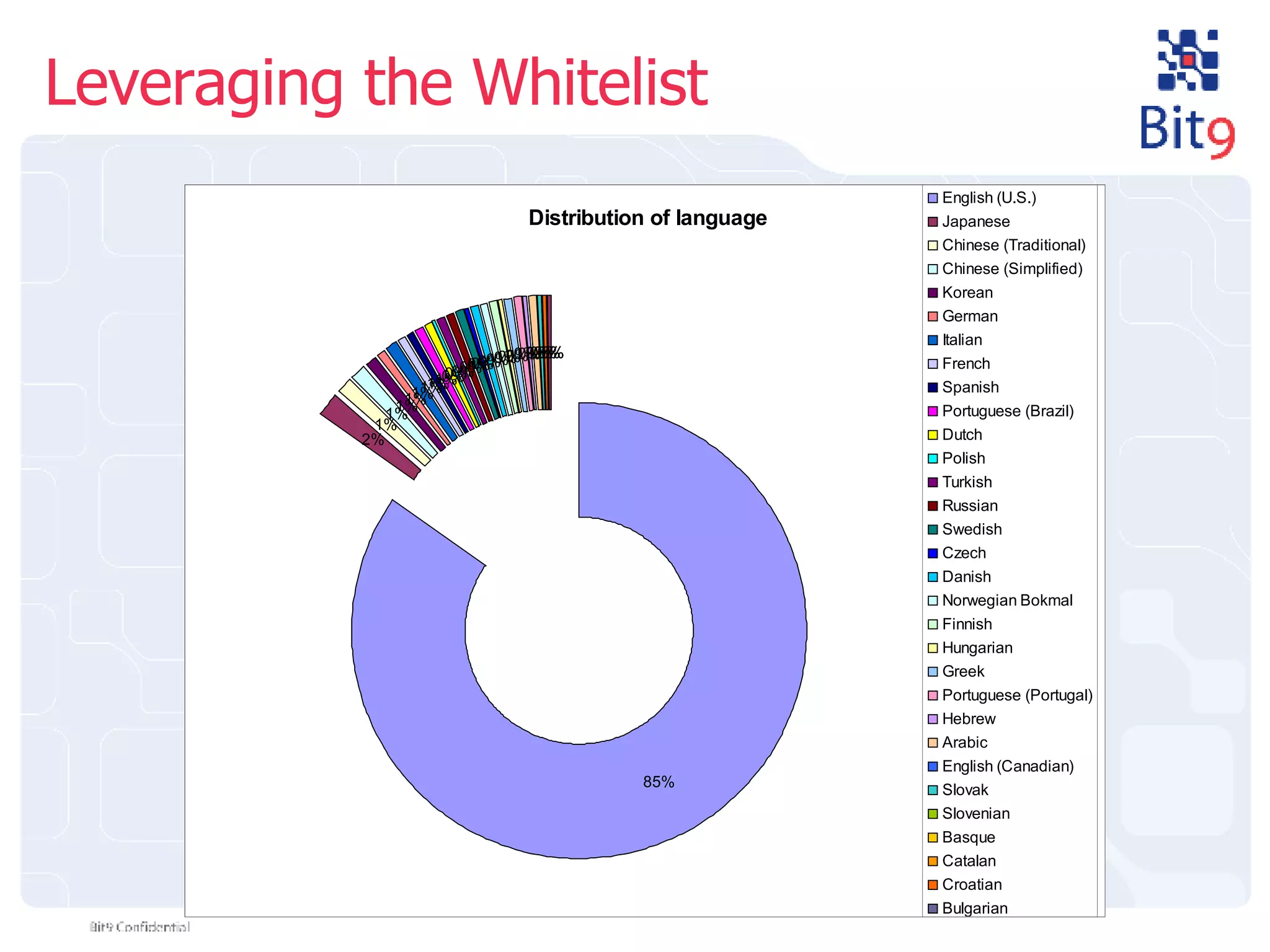
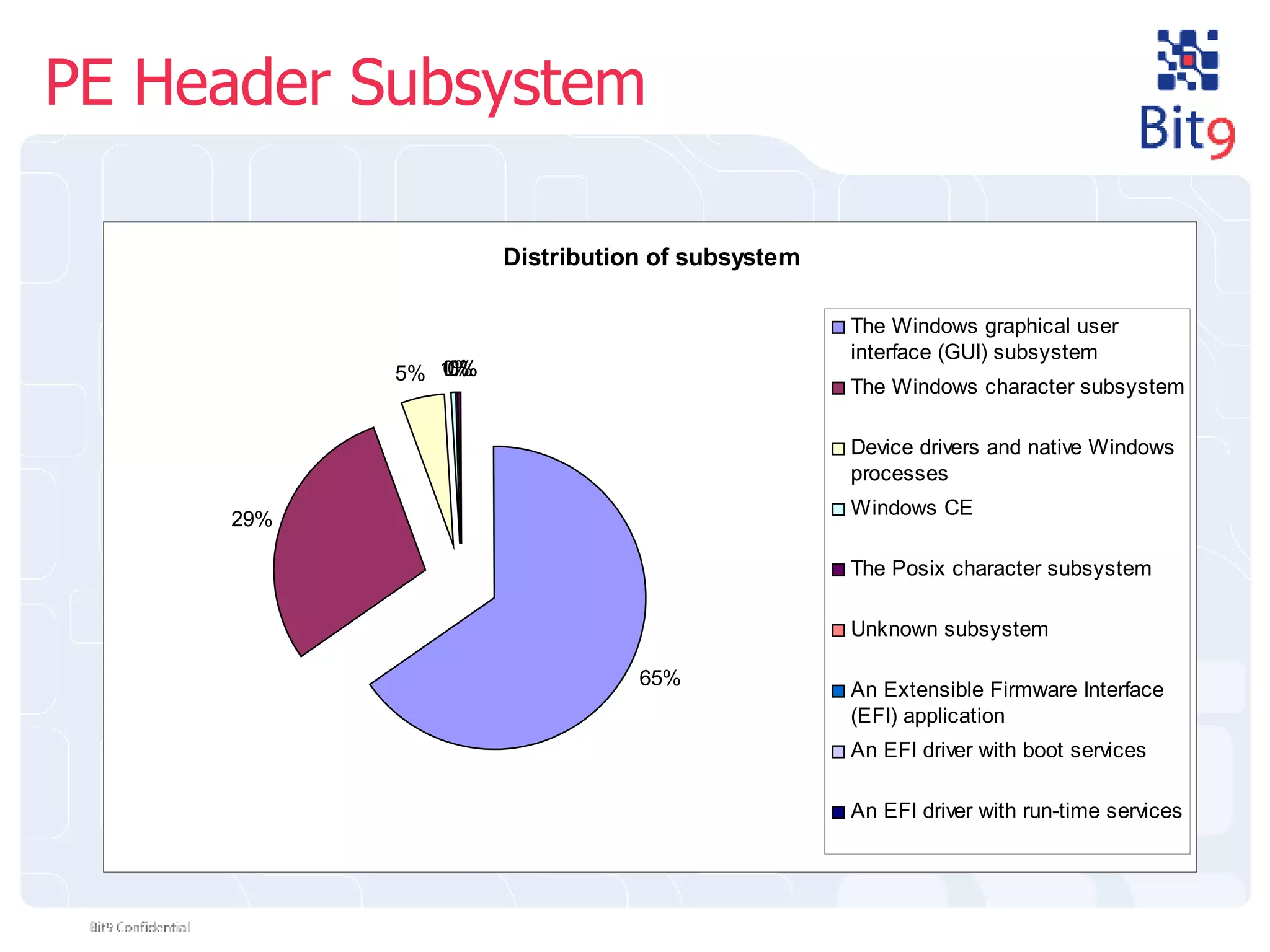
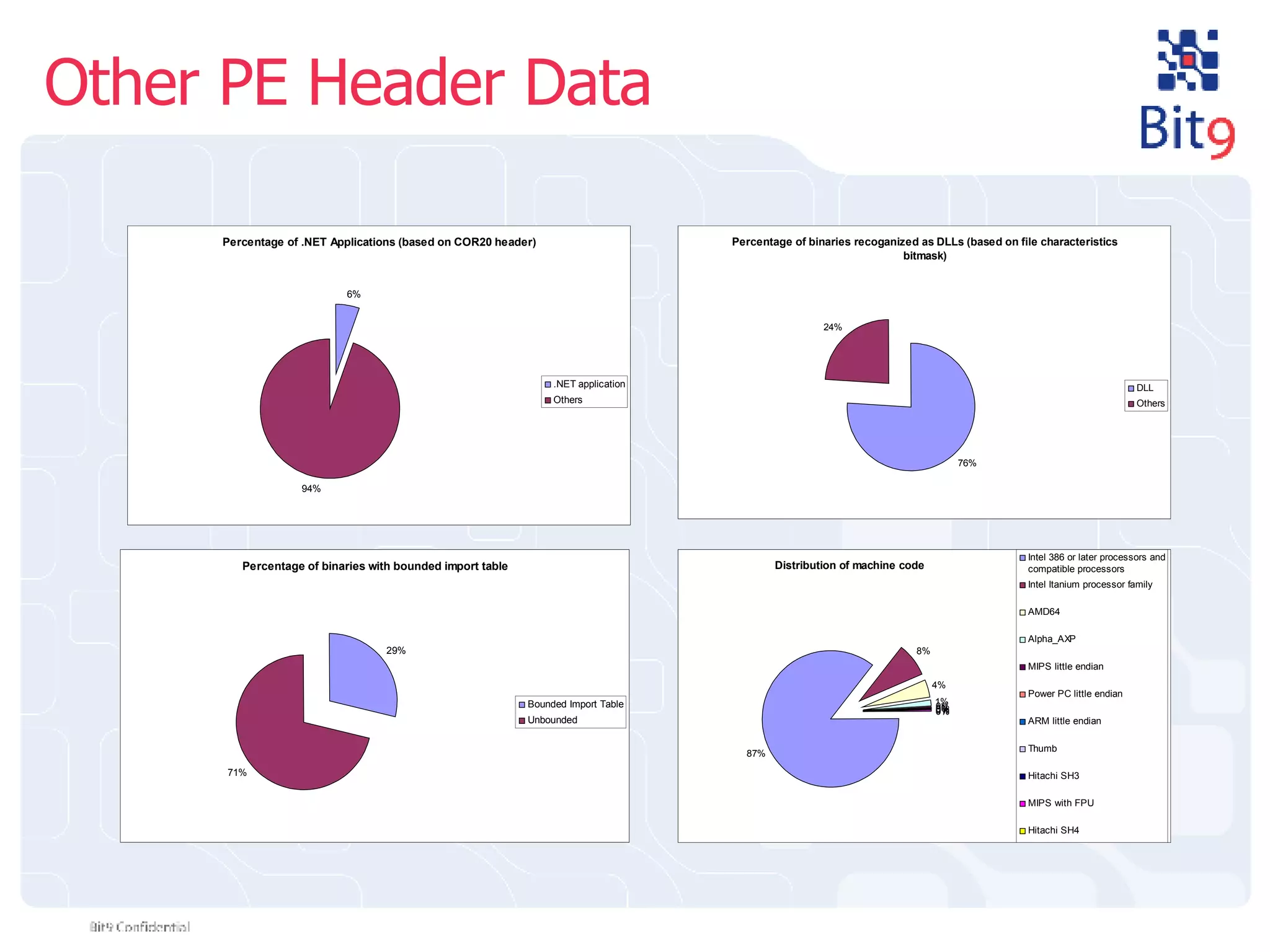
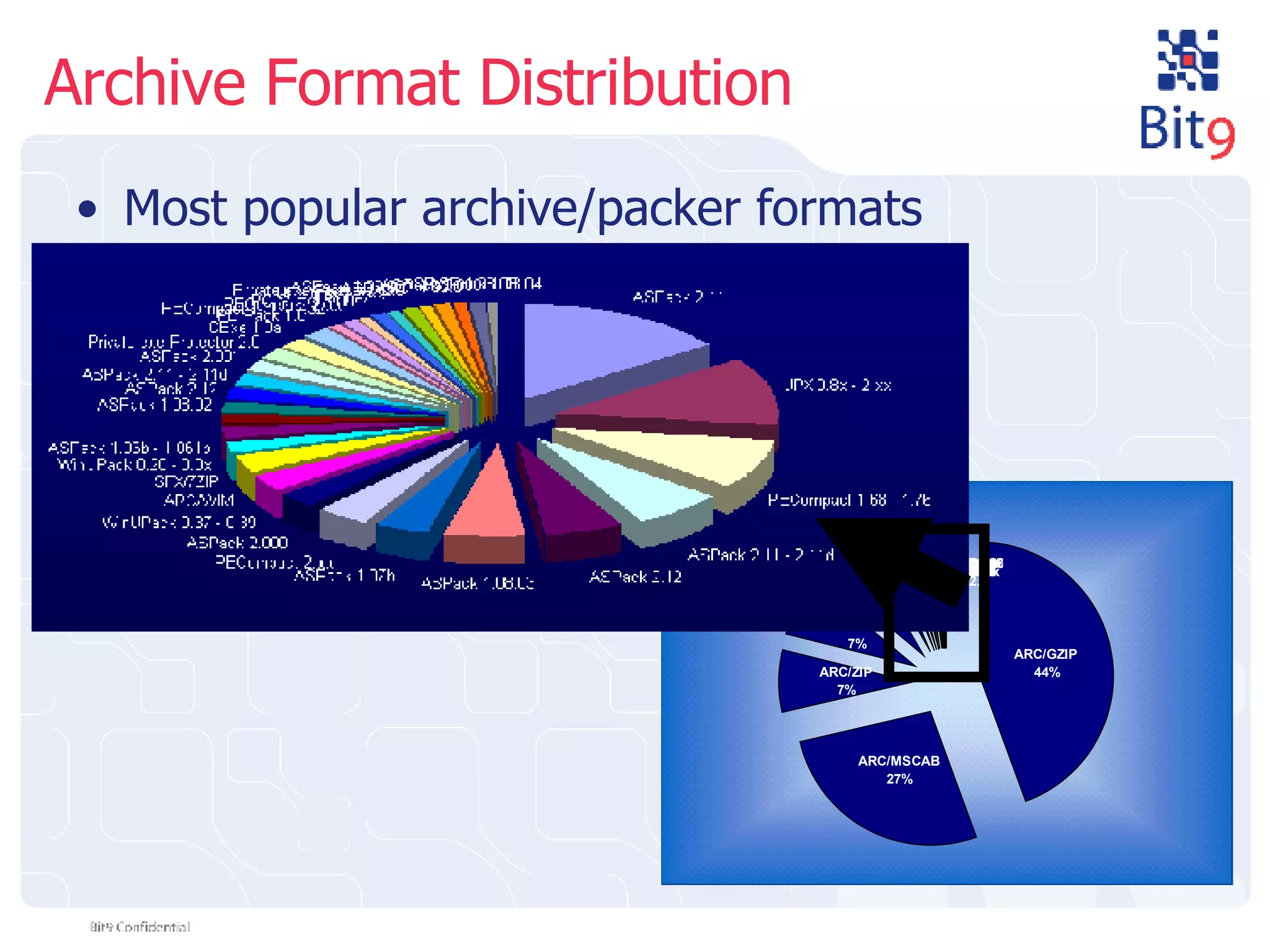
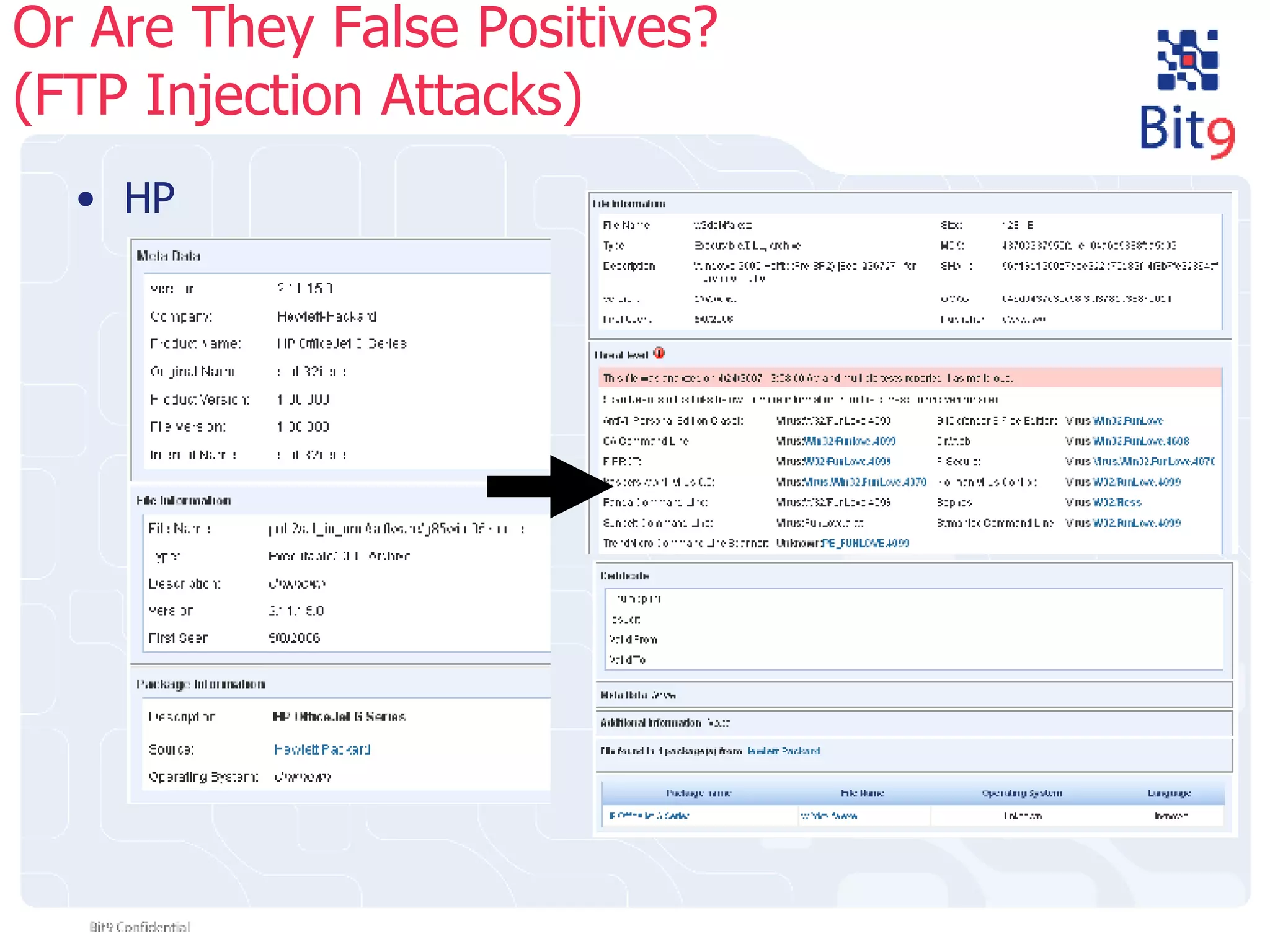
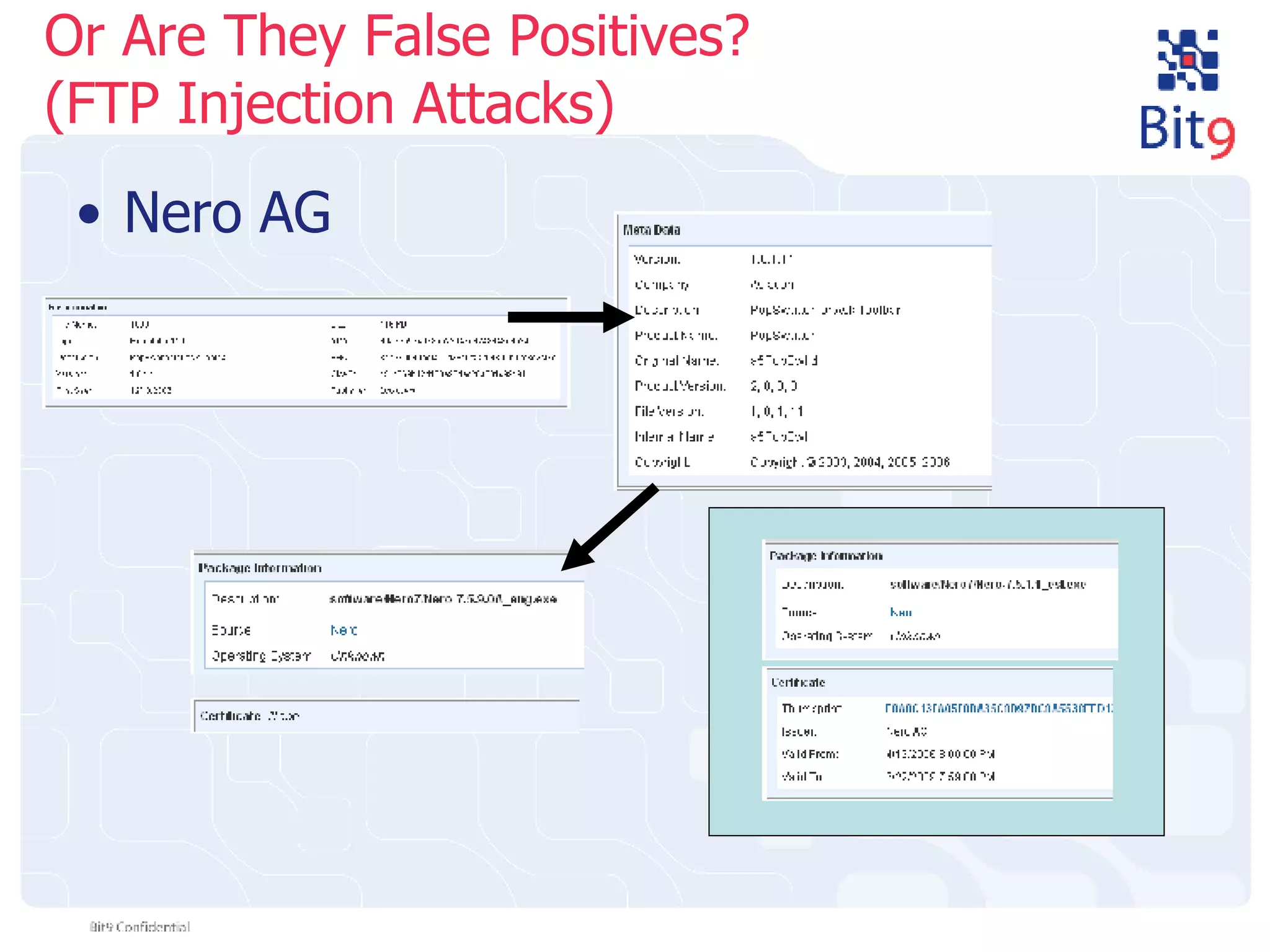
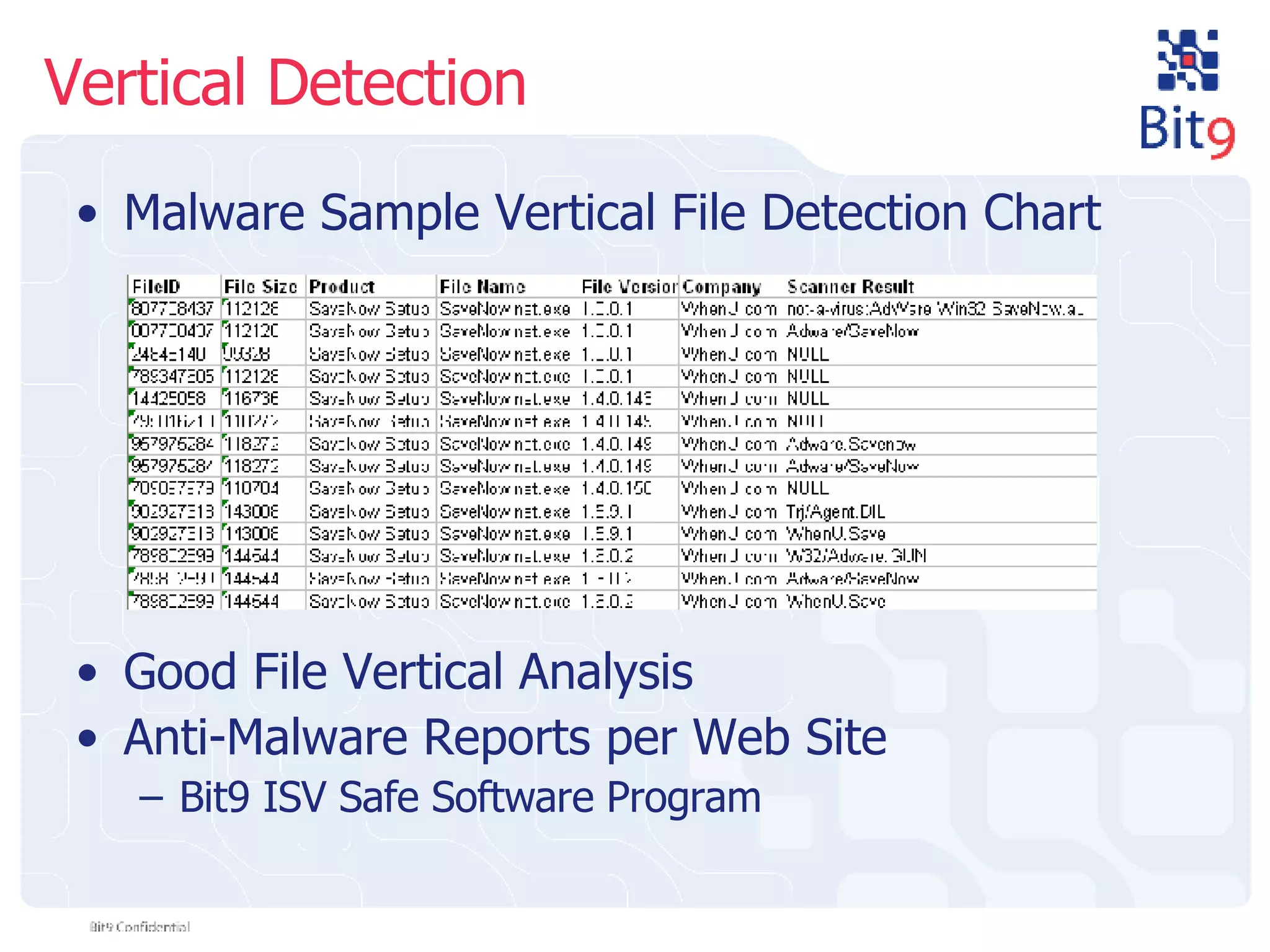
The document discusses the challenges of building and using a global whitelist database for anti-virus testing, highlighting the significant increase in unique malware signatures and the difficulties of acquiring software in a comprehensive manner. It outlines the process of extracting and analyzing software data, the benefits and realities of partnering with trusted sources, and the challenges of certifying software as trustworthy. Additionally, it introduces Bit9's application and device control solutions as a critical resource in combating malware and ensuring software integrity.