Secure wireless modem
•Download as PPT, PDF•
0 likes•179 views
Report
Share
Report
Share
Recommended
More Related Content
What's hot
What's hot (7)
How to upgrade tp link adsl modem router (trend chip solution)

How to upgrade tp link adsl modem router (trend chip solution)
Viewers also liked
Viewers also liked (8)
Similar to Secure wireless modem
Similar to Secure wireless modem (20)
write a Review about Wired Network Security -Network Security Hardware.docx

write a Review about Wired Network Security -Network Security Hardware.docx
Webinar NETGEAR - Nuovi AP Professionali Prosafe WAC720 e WAC730

Webinar NETGEAR - Nuovi AP Professionali Prosafe WAC720 e WAC730
Commissioning, Managing & Troubleshooting Industrial Networks

Commissioning, Managing & Troubleshooting Industrial Networks
More from creativelakshu
More from creativelakshu (6)
Recently uploaded
Recently uploaded (20)
Take control of your SAP testing with UiPath Test Suite

Take control of your SAP testing with UiPath Test Suite
DevEX - reference for building teams, processes, and platforms

DevEX - reference for building teams, processes, and platforms
Unraveling Multimodality with Large Language Models.pdf

Unraveling Multimodality with Large Language Models.pdf
Passkey Providers and Enabling Portability: FIDO Paris Seminar.pptx

Passkey Providers and Enabling Portability: FIDO Paris Seminar.pptx
The Fit for Passkeys for Employee and Consumer Sign-ins: FIDO Paris Seminar.pptx

The Fit for Passkeys for Employee and Consumer Sign-ins: FIDO Paris Seminar.pptx
Gen AI in Business - Global Trends Report 2024.pdf

Gen AI in Business - Global Trends Report 2024.pdf
Dev Dives: Streamline document processing with UiPath Studio Web

Dev Dives: Streamline document processing with UiPath Studio Web
Ensuring Technical Readiness For Copilot in Microsoft 365

Ensuring Technical Readiness For Copilot in Microsoft 365
What's New in Teams Calling, Meetings and Devices March 2024

What's New in Teams Calling, Meetings and Devices March 2024
Digital Identity is Under Attack: FIDO Paris Seminar.pptx

Digital Identity is Under Attack: FIDO Paris Seminar.pptx
Developer Data Modeling Mistakes: From Postgres to NoSQL

Developer Data Modeling Mistakes: From Postgres to NoSQL
Use of FIDO in the Payments and Identity Landscape: FIDO Paris Seminar.pptx

Use of FIDO in the Payments and Identity Landscape: FIDO Paris Seminar.pptx
DevoxxFR 2024 Reproducible Builds with Apache Maven

DevoxxFR 2024 Reproducible Builds with Apache Maven
Generative AI for Technical Writer or Information Developers

Generative AI for Technical Writer or Information Developers
Secure wireless modem
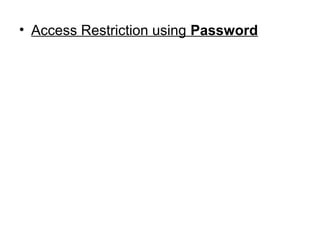
- 1. • Access Restriction using Password
- 2. Login to the ADSL Router on http://192.168.1.1 The username and password by default are ‘admin’ and ‘admin’. Click on ‘advanced’
- 3. Click on ‘wireless security’
- 4. Select the WEP security. Enable WEP security. Key in the desired security password. Click on Apply.
- 5. • Access List (MAC based)
- 6. • To add the clients to the access list, find out the MAC id of the clients (wireless interface card) where the connectivity is required, using the command ipconfig –all. • To find out the MAC id from already active clients, follow the following method.
- 7. •Click on ‘lan clients’ under the ‘advanced’ menu
- 8. Copy the MAC ids for the clients whom access has to be permitted.
- 9. • To add the clients to the access list find the following method.
- 10. •Click on ‘wireless management’ under ‘advanced’ menu.
- 11. Select the check box ‘enable access list’ Select ‘allow’ Enter the MAC id in the space provided. Click on add.
- 12. Click on ‘apply’
- 13. • Save the entire configuration by following the method given below.
Editor's Notes
- Proceed to Wireless Security