Enhancing Computer Security via End-to-End Communication Visualization
- 1. Network Eye: Enhancing Computer Security via End-to-End Communication Visualization Glenn Fink Chris North Department of Computer Science Virginia Polytechnic Institute and State University
- 2. This presentation focuses on a novel computer security visualization technology: Network Eye End-to-End communication visualization concept Network Eye’s place as a tool for computer security visualization Partnership opportunities involving Network Eye
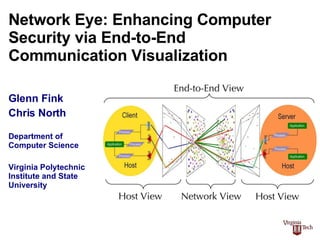
- 3. Network Eye occupies new territory in the computer security tool landscape Charts & Graphs Narrow Broad C OMMUNICATION C ONTEXT Linear Spatial P RESENTATION M ODE Internal Host View Text-Based Dashboards Visualizations Log scanners, Antivirus, ps, top, Tripwire HIDS Networked Host View netstat, lsof, tcpview, host firewalls, vulner-ability checkers, HIDS Spectrum, Orcallator End-to-End View Network View tcpdump, Ethereal, Network Firewalls, NIDS S-Net, NVisionIP ( small multiple and machine views ), AutoFocus, MRTG VisFlowConnect, NVisionIP ( Galaxy View ), EtherApe, RumInt, Rivet (Visible Computer) Big Brother, Nagios NVisionCC? Sguil The Visible Computer applet NETWORK EYE
- 4. Network Eye provides End-to-End visualization by correlating network and host activities Source & Destination Port Maps Source & Destination Network Maps Client Host View Server Host View Network View End-to-End View 23:04:22.813882 10.0.1.2.50128 > 239.255.255.253.svrloc: udp 49 23:04:22.988068 10.0.1.2.50130 > 10.0.1.1.osu-nms: udp 4 23:04:22.989256 10.0.1.1.osu-nms > 10.0.1.2.50130: udp 108 23:04:23.038353 10.0.1.2.50128 > 239.255.255.253.svrloc: udp 49 23:04:23.084775 10.0.1.3.52750 > 10.0.1.1.osu-nms: udp 4 23:04:27.988076 10.0.1.2.50131 > 10.0.1.1.osu-nms: udp 4 23:04:27.989258 10.0.1.1.osu-nms > 10.0.1.2.50131: udp 108 23:04:29.656096 10.0.1.1.domain > 10.0.1.3.60857: 6852 NXDomain* 0/0/0 (39) 23:04:27.988076 10.0.1.2.50131 > 10.0.1.1.osu-nms: udp 4 23:04:27.989258 10.0.1.1.osu-nms > 10.0.1.2.50131: udp 108 23:04:29.656096 10.0.1.1.domain > 10.0.1.3.60857: 6852 NXDomain* 0/0/0 (39) 23:04:35.614864 10.0.1.3.52754 > 10.0.1.1.osu-nms: udp 4 23:04:35.614864 10.0.1.3.52754 > 10.0.1.1.osu-nms: udp 4 23:04:27.988076 10.0.1.2.50131 > 10.0.1.1.osu-nms: udp 4 23:04:27.989258 10.0.1.1.osu-nms > 10.0.1.2.50131: udp 108 23:04:29.656096 10.0.1.1.domain > 10.0.1.3.60857: 6852 NXDomain* 0/0/0 (39) 23:04:35.614864 10.0.1.3.52754 > 10.0.1.1.osu-nms: udp 4 23:04:35.617335 10.0.1.1.osu-nms > 10.0.1.3.52754: udp 108 23:04:37.142782 10.0.1.3.ipp > 10.0.1.255.ipp: udp 100 Text-only Packet Traces PID TT STAT TIME COMMAND 1 ?? Ss 0:00.03 /sbin/init 2 ?? Ss 0:28.26 /sbin/mach_init 51 ?? Ss 0:02.39 kextd 77 ?? Ss 0:56.27 update 81 ?? Ss 0:00.00 dynamic_pager -H 40000000 -L 160000000 -S 80000000 -F 112 ?? Ss 20:43.98 configd 135 ?? Ss 0:01.26 /System/Library/CoreServices/SecurityServer -X 187 ?? Ss 0:02.39 /sbin/autodiskmount -va 280 ?? Ss 0:01.61 syslogd 291 ?? Ss 0:00.01 /usr/libexec/crashreporterd 522 ?? S 0:00.71 /usr/sbin/httpd 635 ?? S 0:00.59 /usr/sbin/httpd 750 ?? S 0:01.48 /System/Library/CoreServices/SecurityAgent.app/Conten 1437 ?? Ss 0:07.20 slpd -f /etc/slpsa.conf 1477 ?? Ss 0:05.56 /usr/sbin/lookupd 1588 ?? S 0:02.51 /Applications/Library/BBEdit Lite 6.1/Bee bee Edit /A 1579 std Ss 0:00.45 login -pf glenn 1580 std S 0:00.06 -tcsh (tcsh) Text-only Process Listings
- 5. Portall is a prototype of Network Eye’s “networked host view” Portall shows clients and servers It shows each process’s network connections Portall can display packet dumps
- 6. Network Eye GL is a “Network View” prototype written in OpenGL Each dot represents a host machine On the left are clients, on the right are servers Most trusted hosts appear near the center Lines of various colors illustrate connections
- 7. Network Eye presents mutually beneficial opportunities for research partnership Business partnership provides relevance and experience for academics Partnership is a win-win proposition Academic partnership provides business with cutting-edge research
Editor's Notes
- Who I am: * Ph.D. student in Computer Security Visualization at VT * Experience: (Army Officer 12yrs. and Naval Civilian Engineer 15yrs.) * Computer security projects and interests * MS in Software Engineering * finkga@vt.edu, <http://csgrad.cs.vt.edu/~finkga> Who Dr. North is: * Assistant Professor of CS at VT and my advisor * Many projects in information visualization, and usability, including $345K gigapixel display project. * Ph.D. in Information Visualization from UMD. * <http://people.cs.vt.edu/~north/> Computer security landscape: * Legislative compliance is becoming a key CIO/CISO function (similar to safety & environmental) * Gramm-Leach-Bliley, Sarbanes-Oxley (Section 404) * Double jeopardy: being attacked and then being sued for the results. Negligence and due-diligence. * Rising requirement for online systems coupled with the rising risk of attack and the decreasing window of effective patching time * Exponentially increasing cybercrime since the inception of the Internet. * Phishing attacks Brief explanation of Network Eye and end-to-end communication visualization.