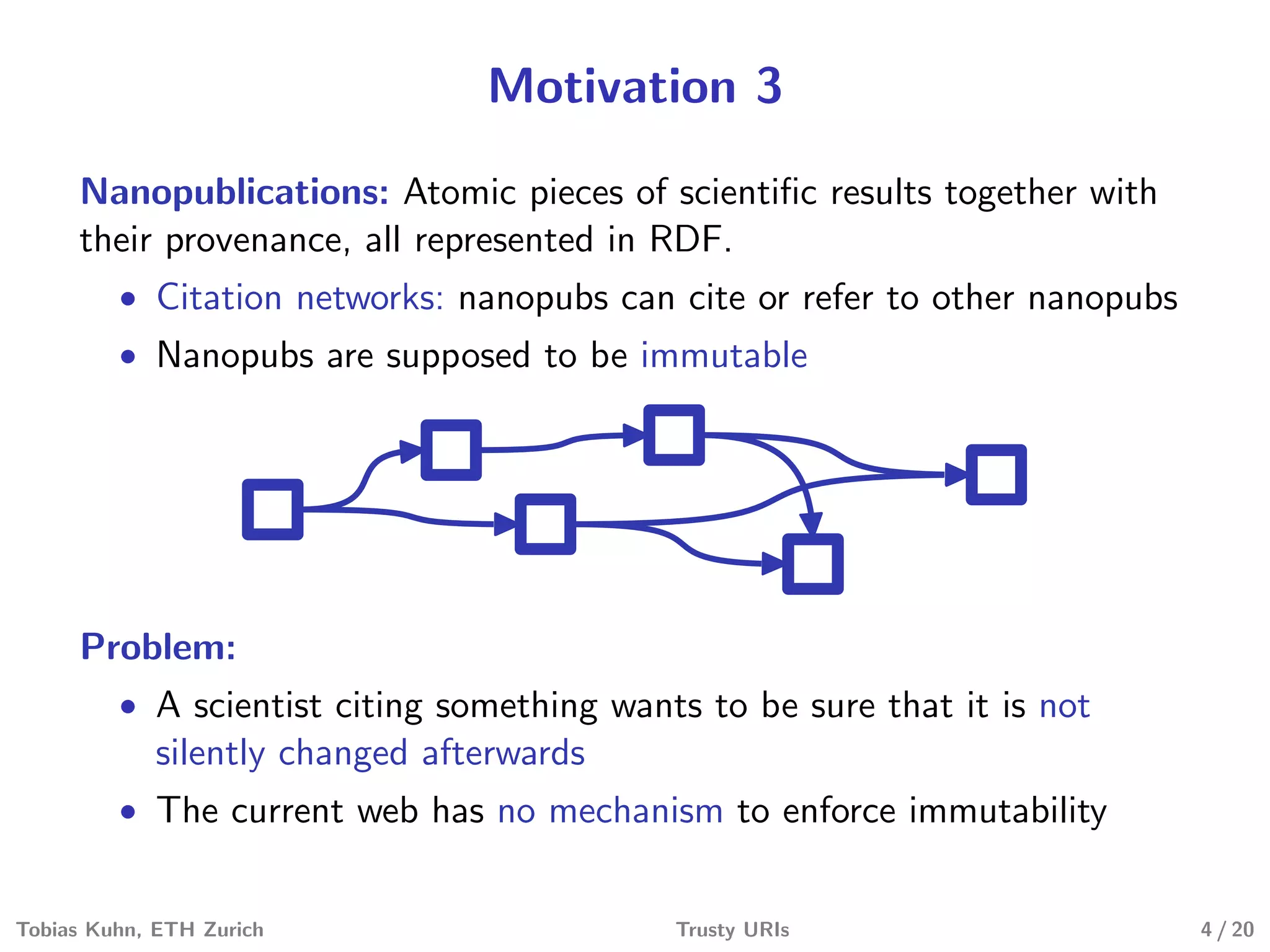
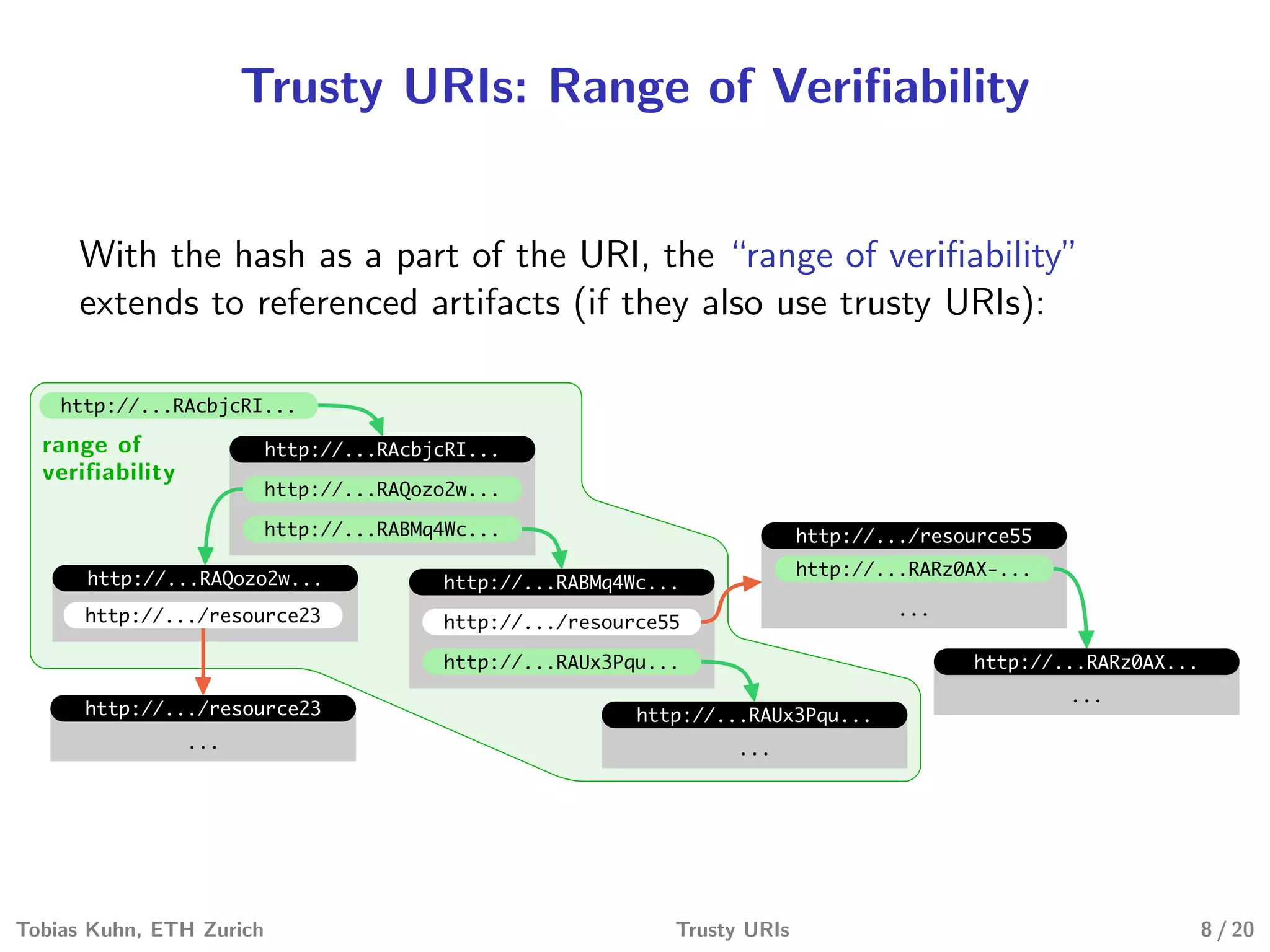
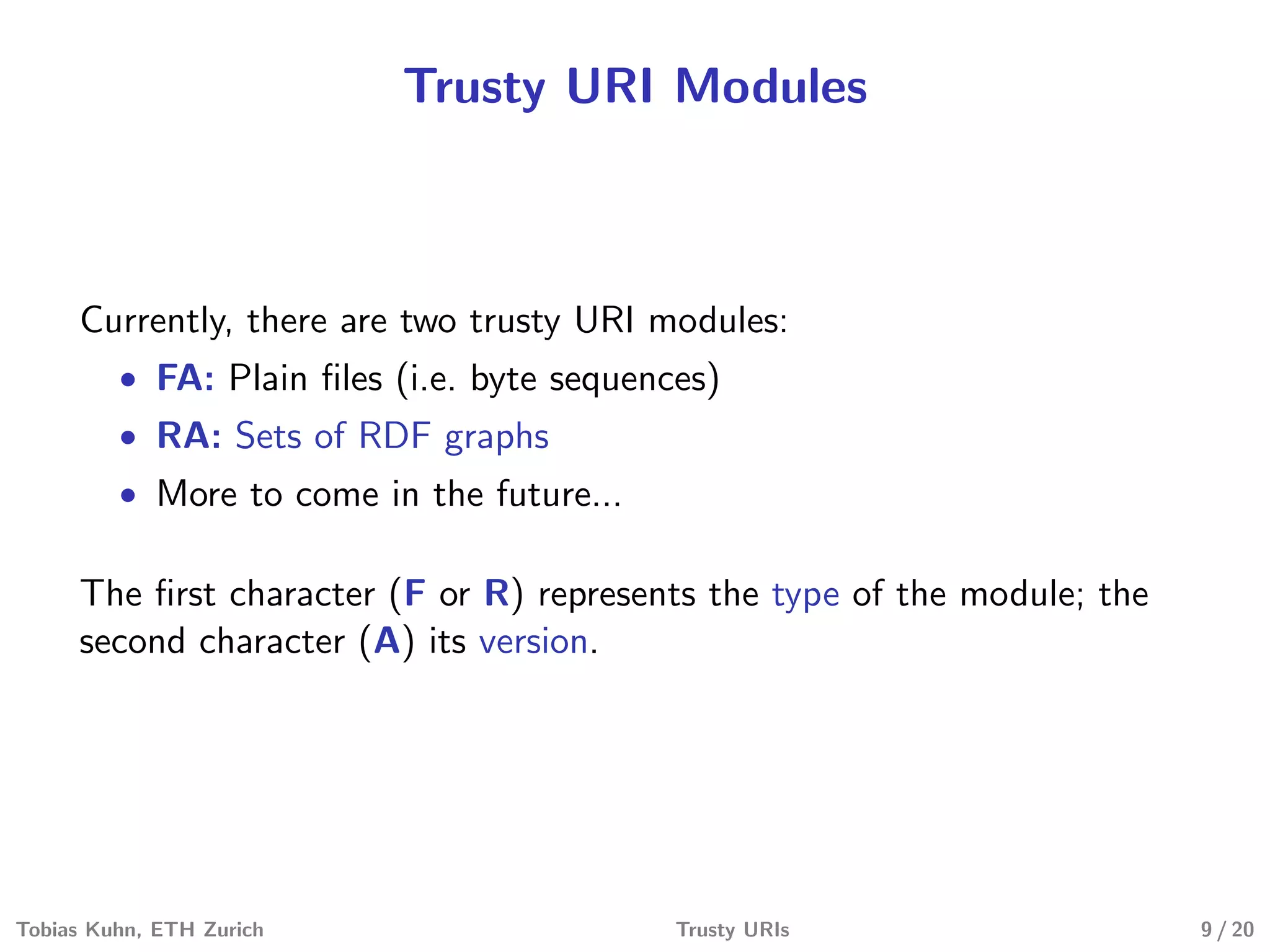
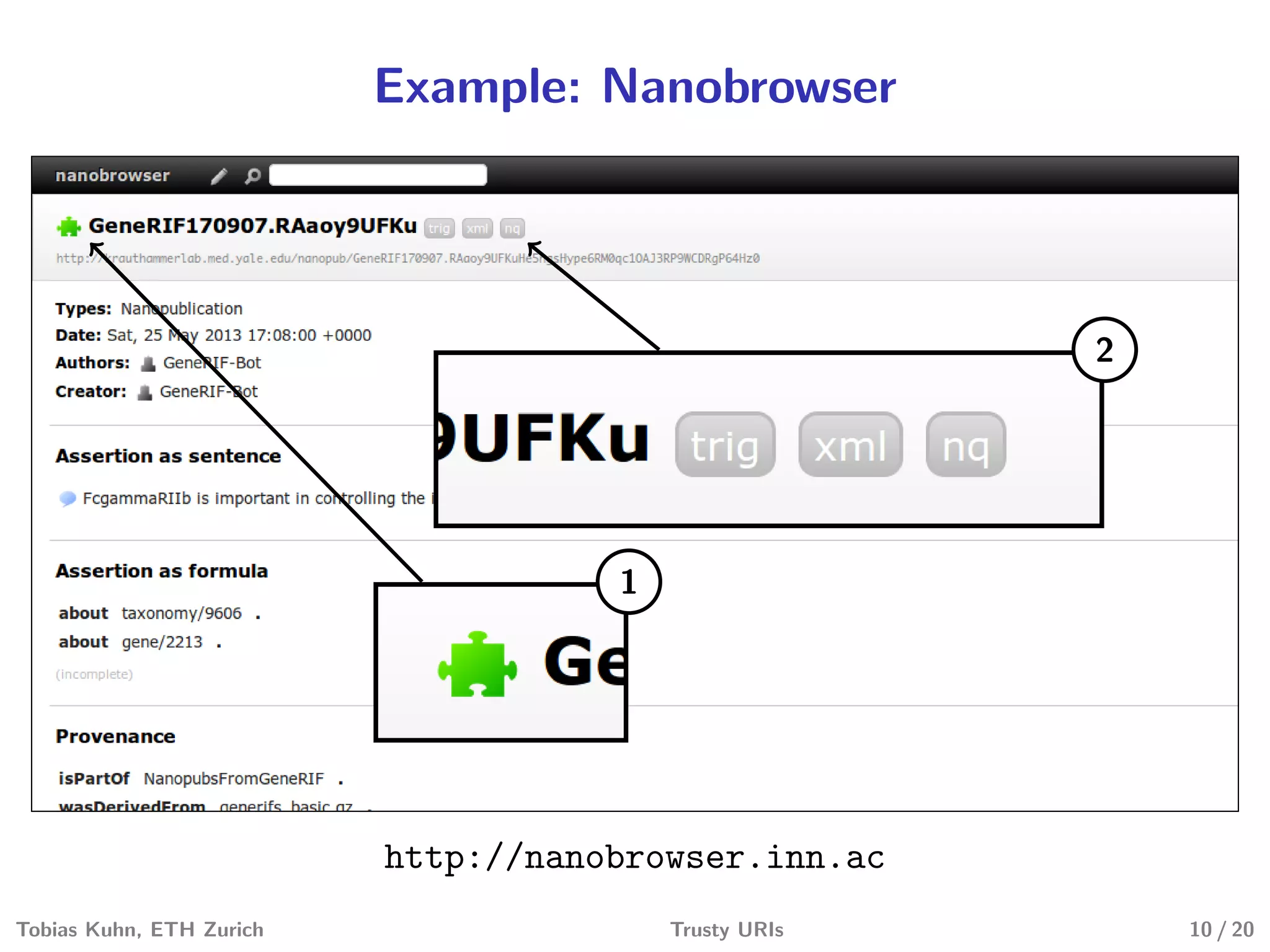
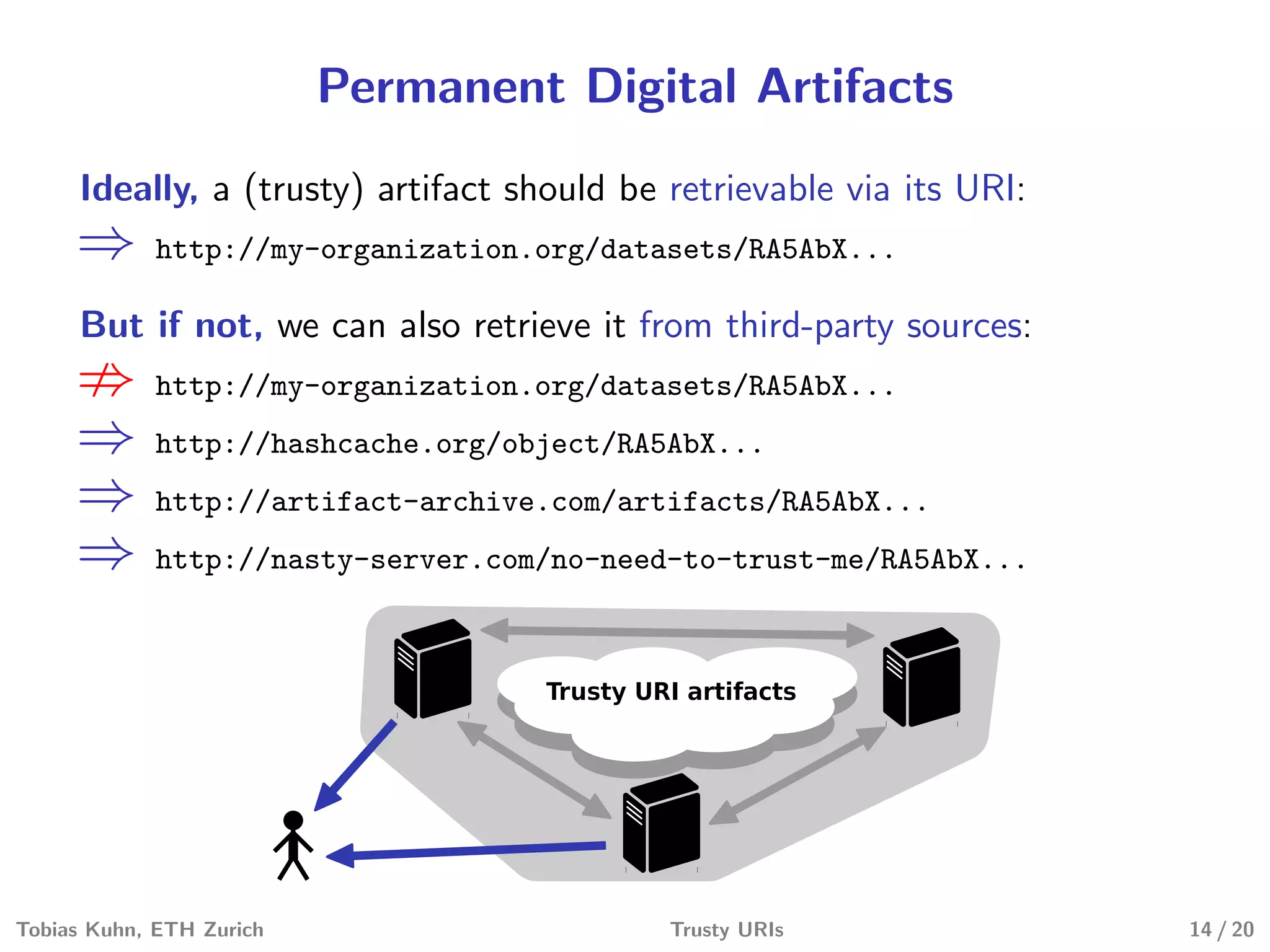
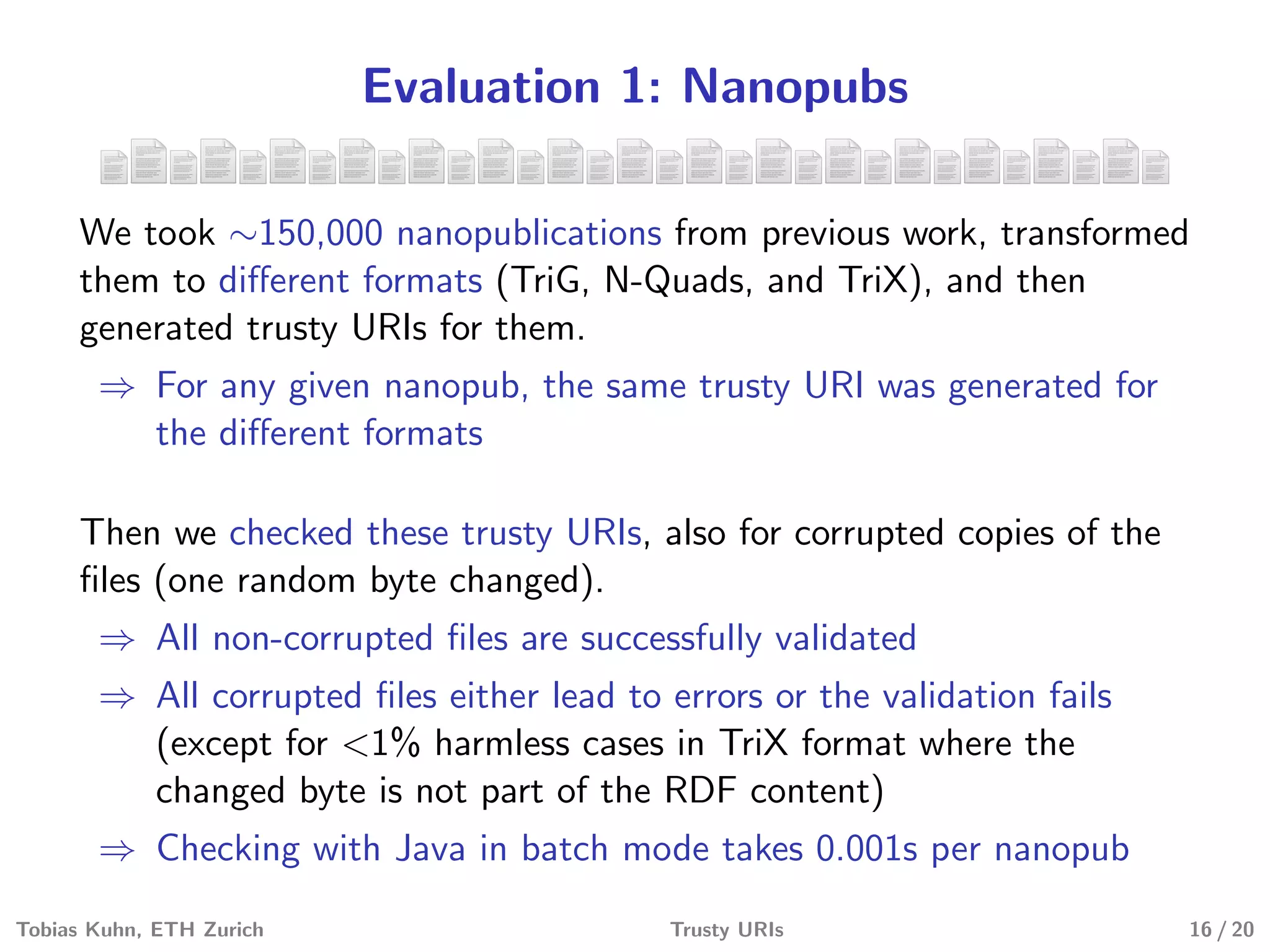
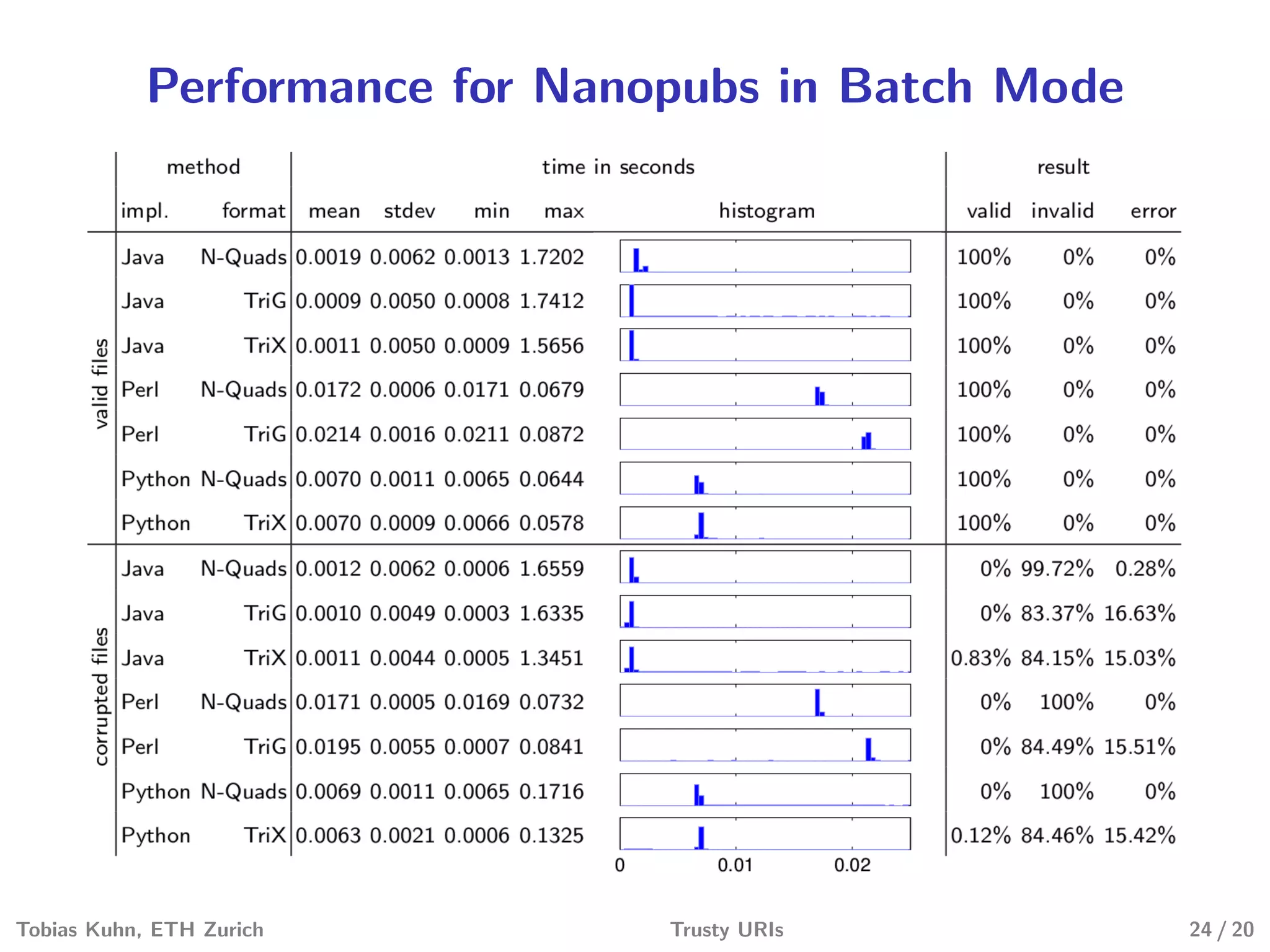
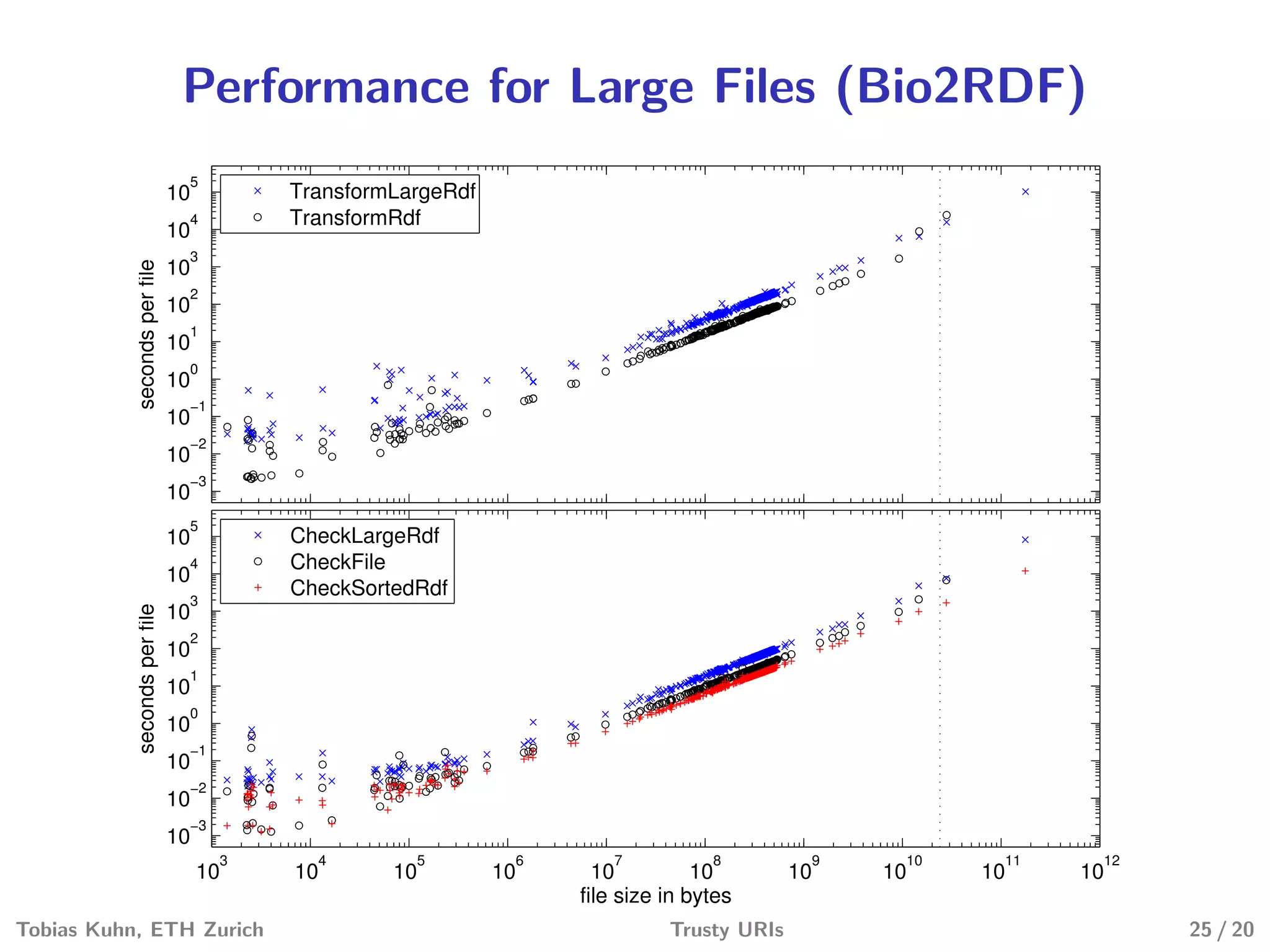
Tobias Kuhn and Michel Dumontier present Trusty URIs, which aim to provide verifiable, immutable, and permanent references to digital artifacts on the Semantic Web. Trusty URIs include a cryptographic hash of the artifact as part of the URI itself. This allows anyone to verify that a URI resolves to the unaltered original artifact. It also ensures URIs remain permanent references even if the original location becomes unavailable. Implementations exist for plain files and RDF graphs, with more modules planned. Evaluations show Trusty URIs successfully validate original artifacts while detecting corrupted copies, and can handle files from kilobytes to terabytes in size. The project is open source with the goal of building a community around developing and